March 21, 2022
A brief Analysis of the Li.Finance Attack
Attacker: 0x878099f08131a18fab6bb0b4cfc6b6dae54b177e
Attacker address 2: 0xc6f2bde06967e04caaf4bf4e43717c3342680d76
Attacked contract: 0x5a9fd7c39a6c488e715437d7b1f3c823d5596ed1
Implementation contract: 0x73a499e043b03fc047189ab1ba72eb595ff1fc8e
TX:
https://etherscan.io/tx/0x4b4143cbe7f5475029cf23d6dcbb56856366d91794426f2e33819b9b1aac4e96
The attacker first transfers 1Eth from Tornado.Cash as a handling fee.

The attacker then calls the swapAndStartBridgeTokensViaCBridge function in the contract and attacks the contract by crafted malicious data (_swapData).
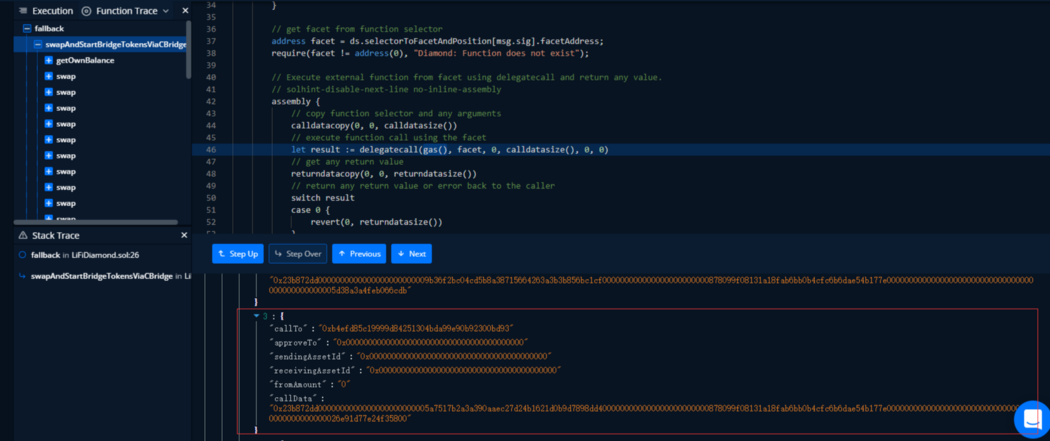
By looking into the source code, we found that the _swapData parameter was controllable. Then we looked into LibSwap.swap and found that the contract was invoked by call.


The attacker exploited the attacked address to approve the contract address and used call to invoke the transferfrom function so as to transfer out the tokens from the address.

Below is the list of funds from attacked addresses.

The total losses are ~$600,000.
Related Project
Related Project Secure Score
Guess you like

Beosin is tracing the whereabouts of the funds in the Ronin attack
March 30, 2022

Attacked 40 Times and Lost Around $1.7 Million: An analysis of Paraluni’s Exploit
March 14, 2022

Beosin Research Series: Are Decentralized Exchanges (DEX) Safe Enough?
March 11, 2022

Beosin’s Analysis of the Arbitrum-based TreasureDAO exploit
March 03, 2022
