March 07, 2024
Another Price Manipulation - Analysis of the attack on the WooPPV2 contract on the Arbitrum
Late at night on March 5, 2024, according to the Beosin Trace platform, the WooPPV2 contract project on the Arbitrum was subject to a price manipulation attack, causing a loss of approximately $8.5 million. The hacker used flash loans to lend USDC.e and Woo tokens and then conducted multiple swaps. Due to flaws in the price calculation of the WooPPV2 contract, the hacker was able to manipulate the price during the exchange process, resulting in the theft of a large number Woo tokens. Beosin security team analyzed this incident immediately.
Vulnerability Analysis
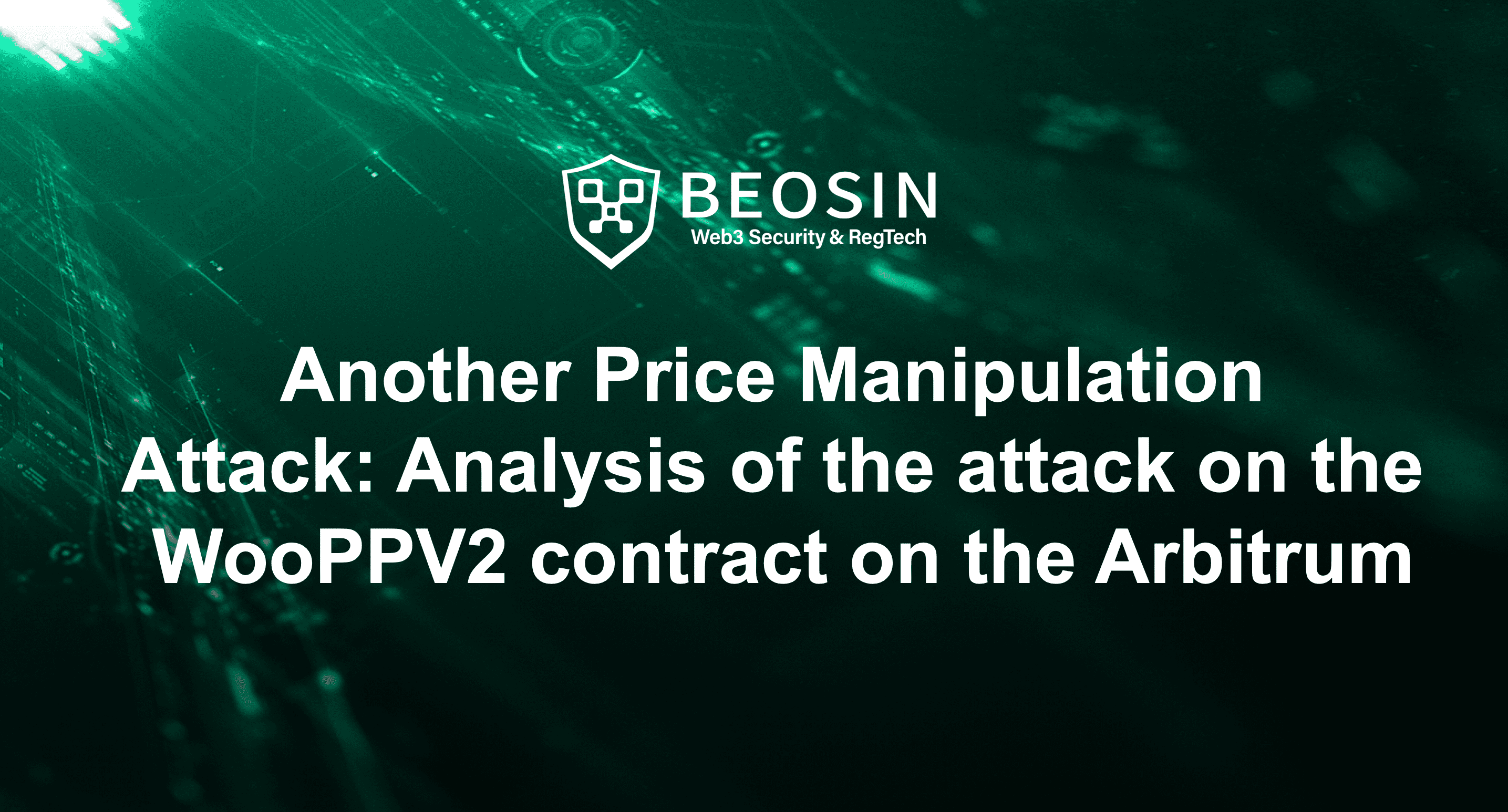
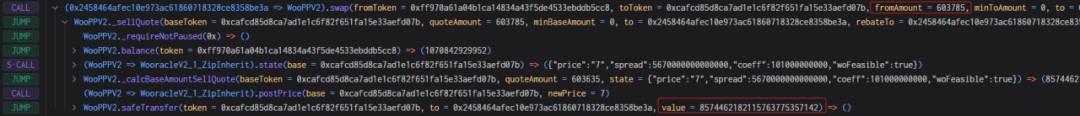
There is a swap function in the WooPPV2 contract. Users can call this function to exchange tokens. This is mainly the exchange between USDC.e and Woo (the following is analyzed based on the exchange between USDC.e and Woo). In the function The quoteToken variable represents USDC.e.
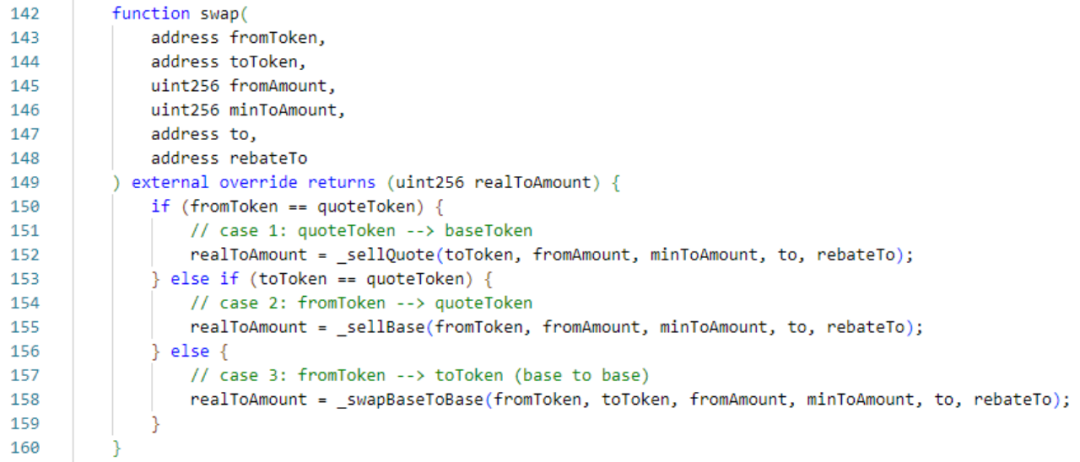
The _sellQuote function has similar logic to the _sellBase function. They both calculate the number of tokens to be exchanged based on the price, and then send the tokens to the caller. _sellQuote is the function called when the caller uses USDC.e to redeem Woo tokens. The main functions are state and _calcBaseAmountSellQuote. state is used to return the structure that saves the Woo price. _calcBaseAmountSellQuote is the function to calculate the exchange amount and the new price.
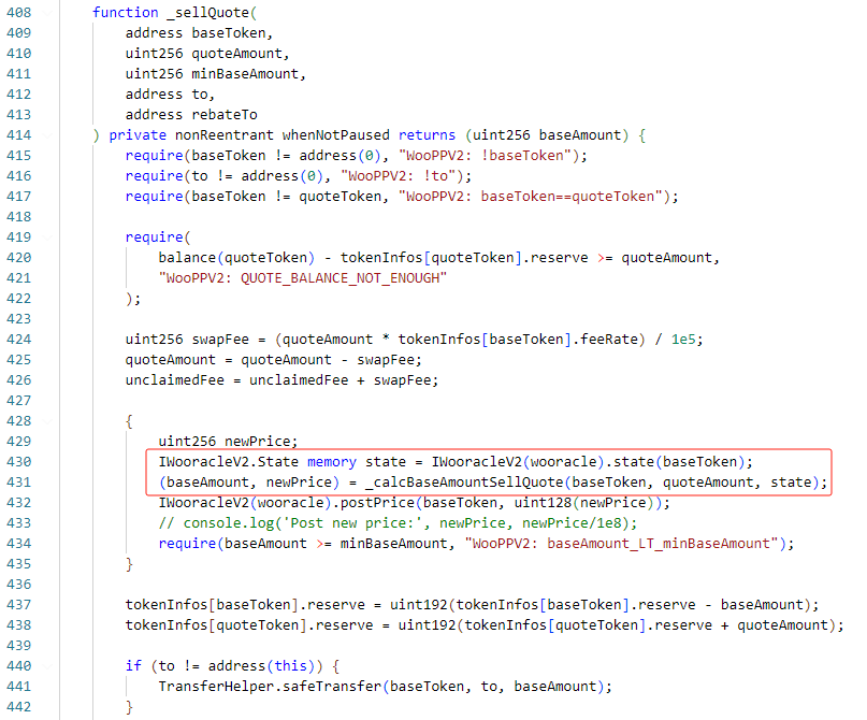
Next, let’s look at the implementation logic of the _calcBaseAmountSellQuote function. baseAmount is the calculated exchange amount. The main logic is to divide the USDC.e amount by the price of Woo to get the amount of Woo that can be exchanged. Next, it is calculated based on the current price and exchange amount. The new price after redemption will be displayed.
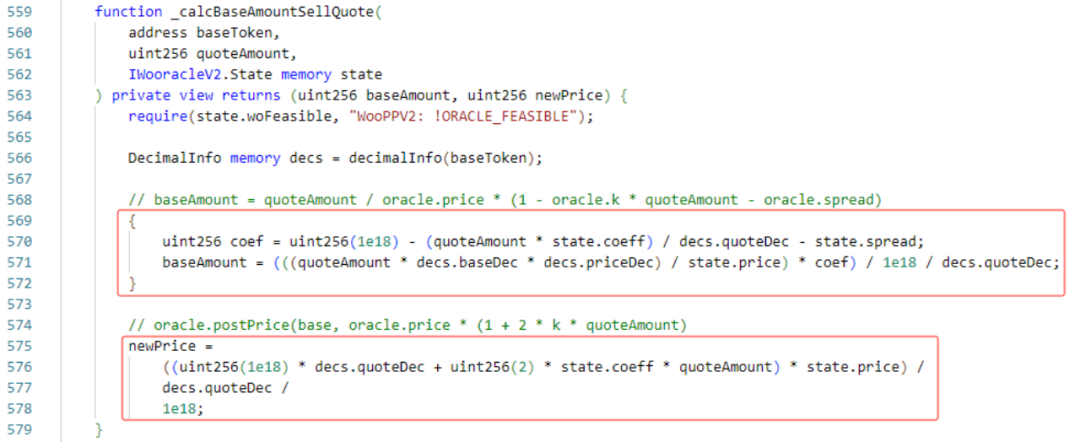
The _sellBase function is the same as the _sellQuote function, except that the _calcQuoteAmountSellBase function is slightly different. The main logic is to multiply the Woo quantity by the Woo price to get the quantity of USDC.e that can be exchanged.
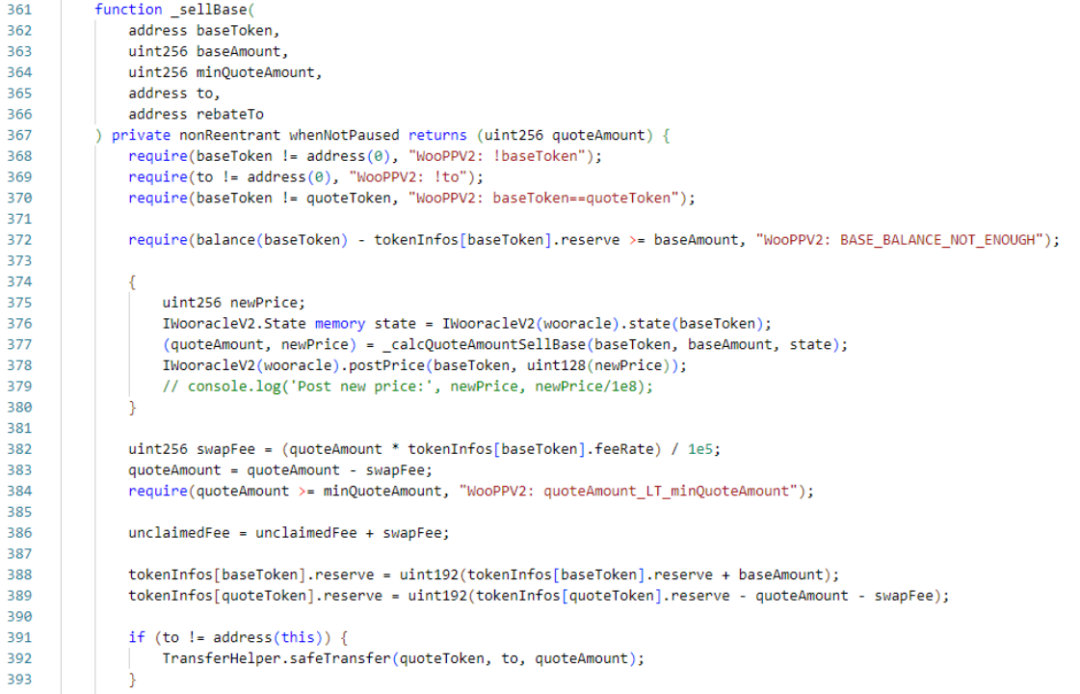
According to the exchange logic, we can find a problem. The calculation logic of this exchange quantity is different from the constant product model of traditional swaps such as Uniswap. This model directly calculates the quantity by multiplying and dividing based on the price, so that there is no slippage in the exchange process, but the price It will change with the exchange. If the caller calculates carefully, he can extract the tokens inside.
For example:
If there are initially 1,000 A tokens and 1,000 B tokens in the pool, the price of B tokens is 1. Then if you use 500 A tokens, you can exchange for 500 B tokens. At this time, the pool becomes 1500:500, and the B token price will increase, for example, to 2. Next, using the 500 B tokens exchanged, 1,000 A tokens will be exchanged. The final pool will become 500:1,000, and 500 A tokens will be extracted out of thin air.
In this incident, the attacker used this security issue. Let's take a look at how the attacker carried out the attack.
Attack Process
In this incident, the attacker used the same method to attack many times. Here is the0xe80a16678b5008d5be1484ec6e9e77dc6307632030553405863ffb38c1f94266 takes this transaction as an example.
1. The attacker lent more than 10 million USDC.e and 2.72 million Woo tokens through flash loans.
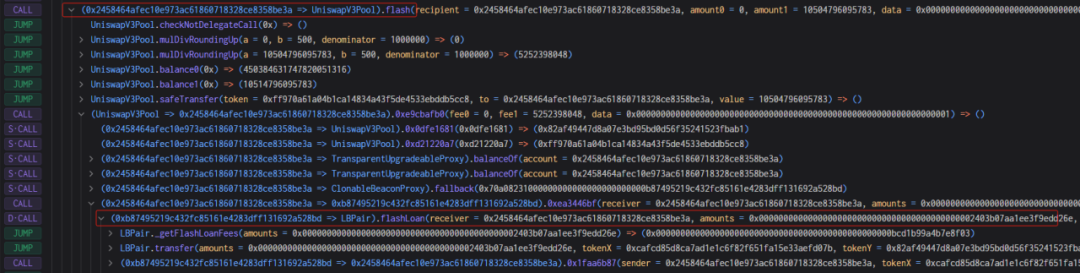
2. Next, the attacker used 100,000 USDC.e to exchange Woo tokens three times. At this time, you can see that the price of Woo is still at the normal price. The attacker currently holds more than 8 million Woo tokens.
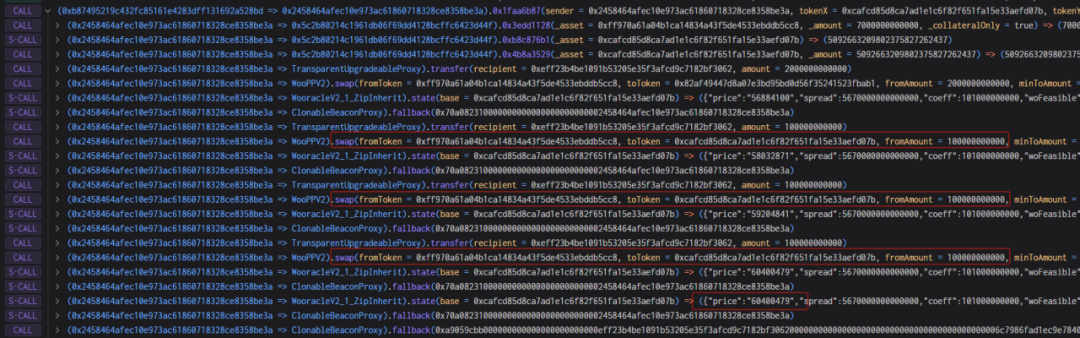
3. Immediately afterwards, the attacker directly used more than 8 million Woo tokens to exchange for USDC.e. Due to the above problems, more than 8 million Woo tokens were all exchanged at normal prices at this time, and more than 2 million USDC were exchanged. e, and according to the above formula, the price of Woo at this time is calculated to be 7, which is reduced by nearly 10 million times.
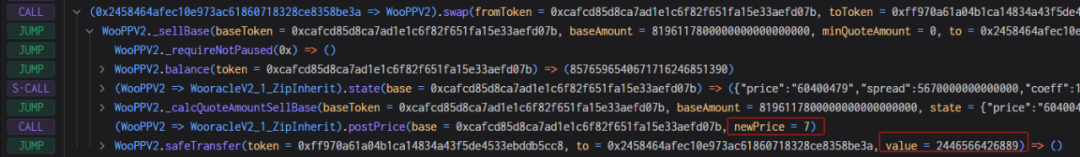
4. Finally, due to the extremely low price of Woo tokens, the attacker used very little USDC.e to exchange more than 8 million Woo tokens, and finally returned the flash loan.
Fund Tracing
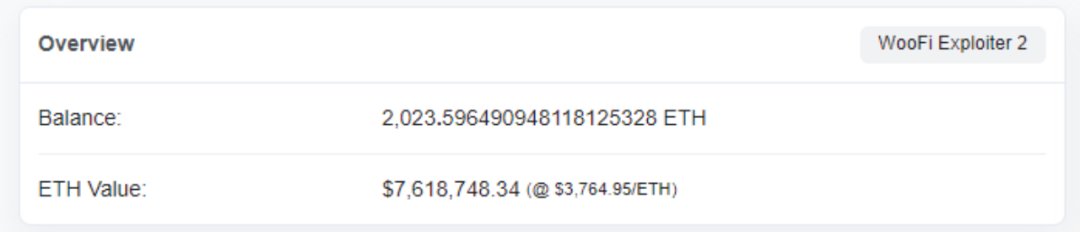
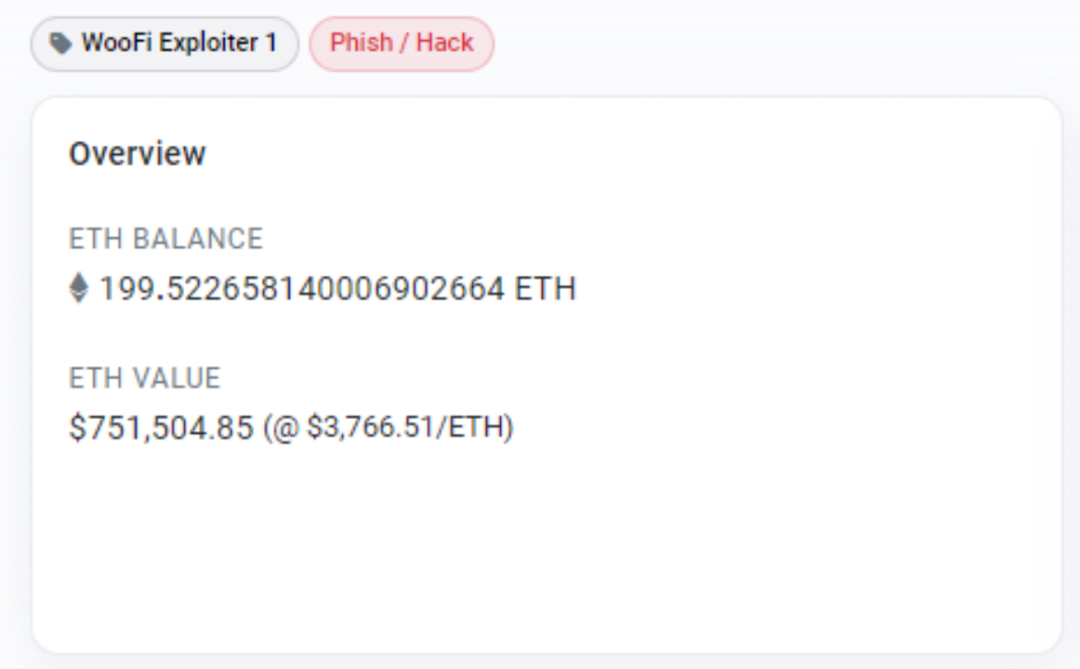
After the hack, the attacker transferred 200 ETH to an address on the Ethereum through a cross-chain bridge and the remaining 2,000+ ETH were stored on an address on the Arbitrum chain . As of press time, none of the funds had been moved.
In view of the price manipulation attack that occurred on the Arbitrum, we must recognize the importance of security risks in the field of virtual assets. Beosin security team will continue to closely monitor and analyze the occurrence of similar incidents to provide timely security solutions and risk control recommendations.
Recently, Beosin has focused on the innovation of various 404 protocols and provided security audit services for ERC404/ARC404 and other protocols. At the same time, Beosin has recently audited a GameFi project based on ARC404 - LONT Games, which is an innovative gaming using ARC404 and BRC20.

Beosin is committed to protecting users and projects from potential security threats and ensuring the safe and stable operation of the blockchain ecosystem. If you have any security needs or questions, please feel free to contact us and we will be happy to support you.
As one of the first blockchain security companies in the world to engage in formal verification, Beosin focuses on the "security + compliance" full ecological business. It has established branches in more than 10 countries and regions around the world, and its business covers code security audits before projects go online. , "one-stop" blockchain compliance products + security services such as security risk monitoring and blocking during project operation, stolen recovery, virtual asset anti-money laundering (AML), and compliance assessments that meet local regulatory requirements.
Related Project
Related Project Secure Score
Guess you like
Lack of function checking - Analysis of SenecaUSD security incident
March 04, 2024

Nibiru is about to launch its mainnet. What are its technical characteristics and security development practices.
March 12, 2024

From SBF to CZ, why crypto trading institutions are always accused of money laundering
March 22, 2024

The outbreak of BOME! Analysis of the MEV issues behind Solana meme season
March 22, 2024
