March 30, 2022
Beosin analysis of the flow of funds in response to the Ronin security incident
According to the tracking results of the Beosin-Trace safety tracking platform:
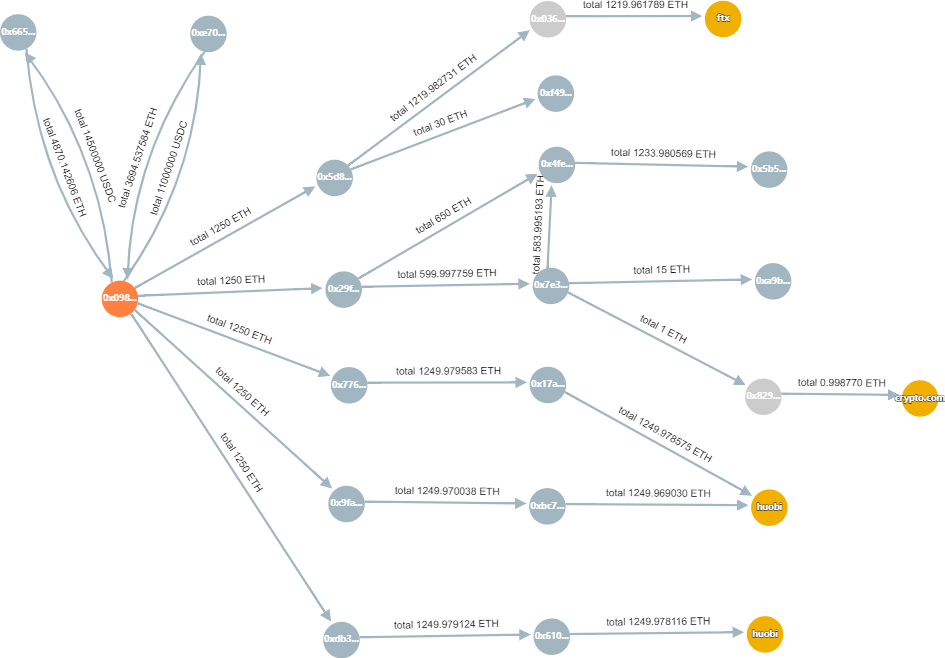
Hacker address: 0x098b716b8aaf21512996dc57eb0615e2383e2f96
Funds stolen from addresses:
0x1A2a1c938CE3eC39b6D47113c7955bAa9DD454F2
Up to now, after the stolen amount has flowed through 15 transit addresses, it has flowed into the exchange addresses:
HUOBI: 0x73f8fc2e74302eb2efda125a326655acfodc2d1b, total 2500ETH
HUOBI: 0x28ffe35688ffffd0659aee2e34778b0ae4e193ad, 1250ETH
FTX: 0xc098b2a3aa256d2140208c3de6543aaef5cd3a94, 1229.96ETH
Crypto.com: 0x6262998ced04146fa42253a5c0af90ca02dfd2a3, 0.99ETH
Hacker address balance: 175,913.70 ETH
Beosin-Trace security tracking platform will keep tracking the flow of stolen funds in real time.
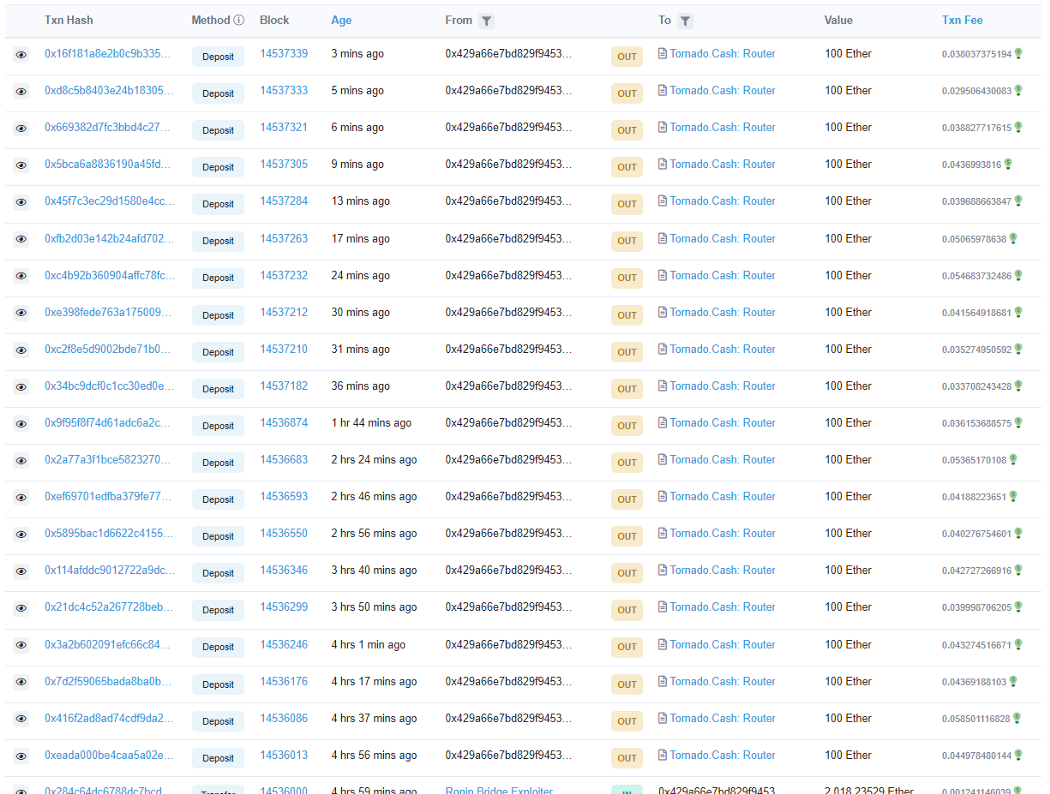
@Ronin_Network ’s exploiter transferred 2,018 ETH to the new address (0x429a66e7bD829F9453CEE5239Bfeaf5657A11A3e) and transferred 2,000 ETH to @TornadoCash in 20 installments.
Related Project
Related Project Secure Score
Guess you like

Monthly Recap — Over 30 Blockchain Security Incidents Occurred in March
April 02, 2022

Beosin is tracing the whereabouts of the funds in the Ronin attack
March 30, 2022

A brief Analysis of the Li.Finance Attack
March 21, 2022

Attacked 40 Times and Lost Around $1.7 Million: An analysis of Paraluni’s Exploit
March 14, 2022
