May 09, 2022
Beosin’s Detailed Analysis of Fortress’s Oracle Manipulation Attack
On May 9, 2022, according to Beosin EagleEye, Fortress’s Chain contract of FortressPriceOracle was exploited for about 1028.1 ETH and 400,000 DAi by an oracle manipulation attack. Beosin security team analyzed the incident and the findings are shown below.
Fortress Introduction
Fortress Credit and Lending (Fortress) is an algorithmic money market and synthetic stable coin protocol designed to bring secure and trustless credit and lending to users. The official website: https://fortress.loans/
Relevant Information
Transaction hash:
0x13d19809b19ac512da6d110764caee75e2157ea62cb70937c8d9471afcb061bf
Hacker address:
0xa6af2872176320015f8ddb2ba013b38cb35d22ad
Hacker contract:
0xcd337b920678cf35143322ab31ab8977c3463a45
Victim contract:
0x00fcF33BFa9e3fF791b2b819Ab2446861a318285
Exploitation Flow
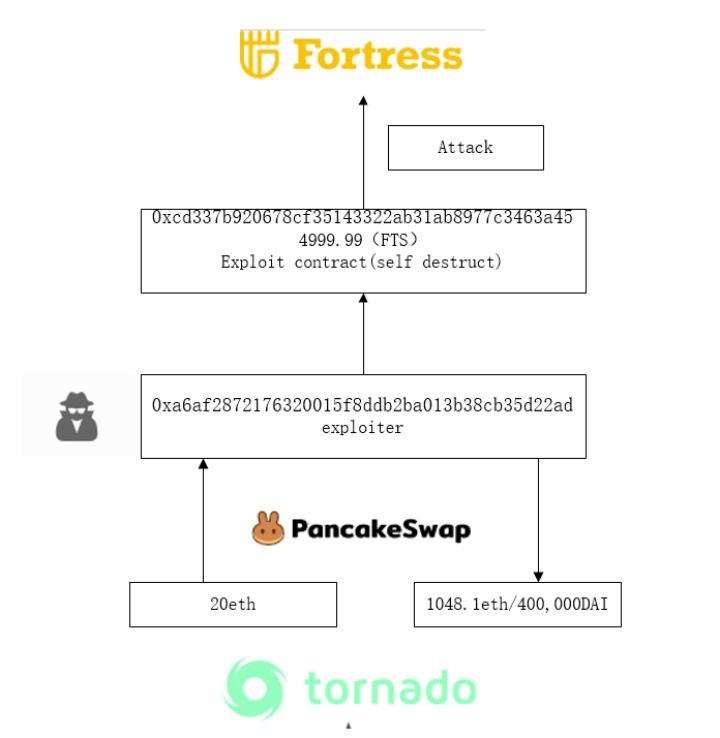
- The attacker withdraws 20ETH from Tornado.cash, deposits 12.4ETH into Celer network and then transfers to the attack contract.
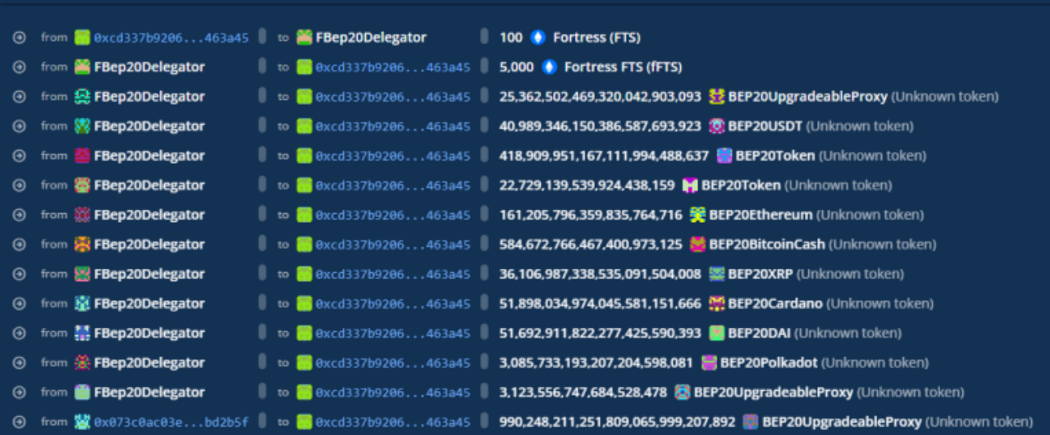
2. The attacker uses the deployed contract to submit a malicious price to make the FTS value extremely high, and then uses the increased value of the FTS to swap out all tokens from FBep20Delelgator.
3. The attacker submits a change in the FTS price when launching the attack, at which point the Oracle calls the function in the chain to get the price.
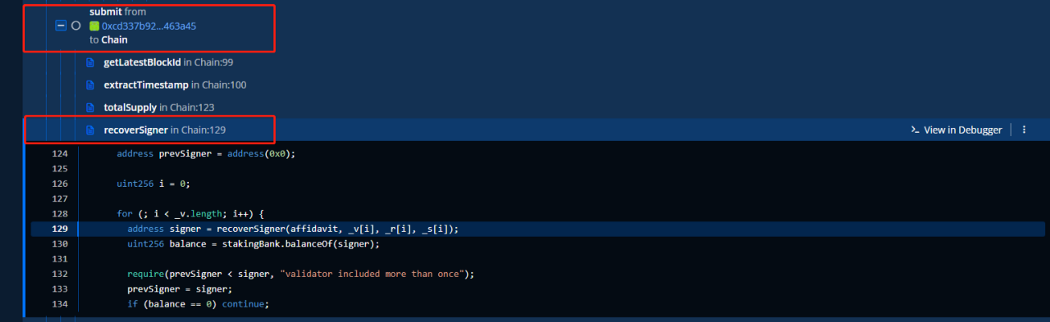
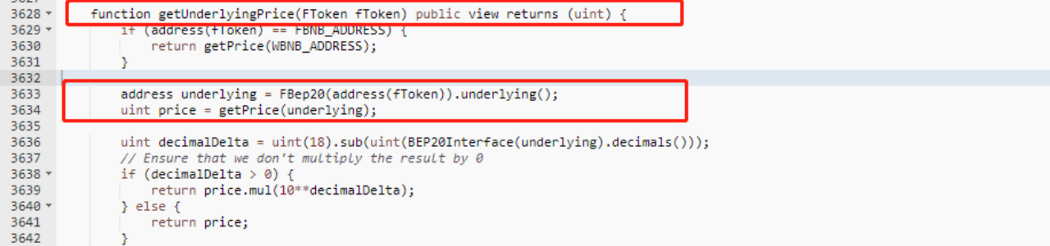
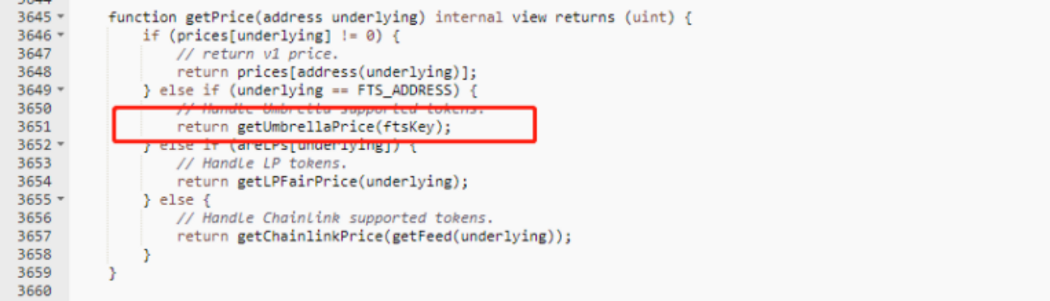
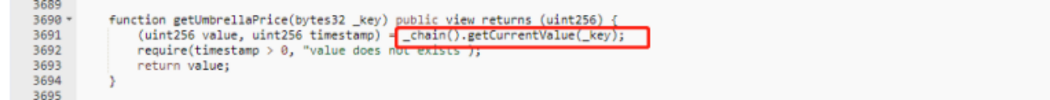
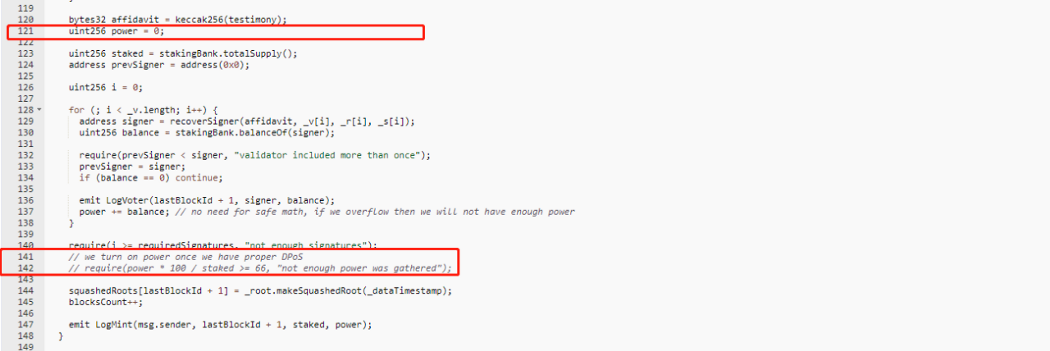
4. Chain’s submit function used for dpos permissions validation is commented, and the value of power = 0. As long as the signature is passed, any address can successfully submit and change the price.
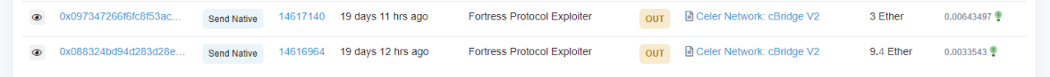
5. The attacker finally swaps the stolen funds into ETH.
Vulnerability Analysis
This attack mainly exploits the vulnerability that the data source Chain obtained by Oracle does not validate power, thus manipulating the collateral price.
Fund Tracing
As of this writing, the attack contract was self-destructed. The stolen 1048.1 ETH and 400,000 DAI were deposited into TornadoCash.
Summary
In response to this incident, Beosin security team recommends:
1. Validating the source of the price data acquired by Oracle is important. It is recommended to use TWAP.
2. Before the project goes live, it is highly recommended to choose a professional security audit company for a comprehensive security audit to avoid security risks.
More
1. VaaS — Automatic Detection Tool , Make Your Smart Contract Secure In Web3.0
2. How to Ensure the Security of NFT Under the Web 3.0 Boom?
3. DEUS Finance Suffered its Second Flashloan Attack This Year: Beosin’s Detailed Analysis
4. Beosin Has Completed Security Audit Service of Crypto LEGO ALG
6. 「RECAP」AMA About How to Keep Your Smart Contract Secure During Development With Beosin VaaS
Contact
If you have need any blockchain security services, please contact us:
Website Email Official Twitter Alert Telegram LinkedIn
Join Coinmonks Telegram Channel and Youtube Channel learn about crypto trading and investing
Also, Read
Related Project
Related Project Secure Score
Guess you like

What is the impact on Web3 after LUNA’s crash and DeFi “fled” ?
May 13, 2022

Beosin Has Completed Security Audit Service of Alpha Quark: No Critical
May 05, 2022

Loss Exceeds $80M Due to Reentrancy Vulnerability in Contract
April 30, 2022

Monthly Recap: More than 21 Typical Security Incidents Occurred in April 2022
April 29, 2022
