April 19, 2022
Beosin’s Analysis of the 2omb Flash Loan Attack
On April 18th, 2022, according to Beosin-Eagle Eye, 2omb’s contract on FTM has suffered a flashloan attack, leading to a gain of 74246.54966 WFTM for the hacker. Beosin security team analyzed the incident and the findings are shown below.
2omb Introduction
2|3omb is part of the Fantom Network ($FTM). 2|3omb provides both use cases and liquidity to the Fantom Network. The official website is https://2omb.finance/.
Relevant Information
Transaction hash:
(Over 70 repeated attacks were conducted; only one representative transaction is listed here)
0xb134f5d0609863aeaab8b8aeb77765a7a0f1e6a379c27455845e46d2261c46a9
Exploiter’s address:
0xd106bb2f7b4bf6ffa12c2db1cbd0d3c25ee18ef9
Contract that launched the hack:
0x77a5d0cdd1f4069747d9236b50f09f34b6d5b378
Victim contract:
0x5D59cDaB08C8BbE4986173a628f8305D52B1b4AE
Exploitation Flow
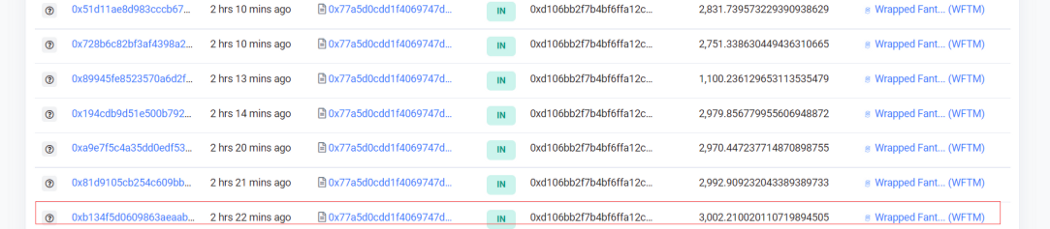
1. Flashloan 139,504 2omb tokens in uniswap’s 2omb-wftm trading pair and send them to the attack contract 0x77a5d0cdd1f4069747d9236b50f09f34b6d5b378.
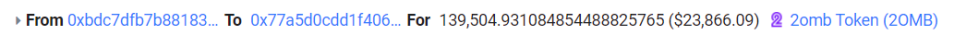
2. Use the attack contract to split the funds, and swap in RedemptionPair (0x5D59cDaB08C8BbE4986173a628f8305D52B1b4AE) for multiple times.

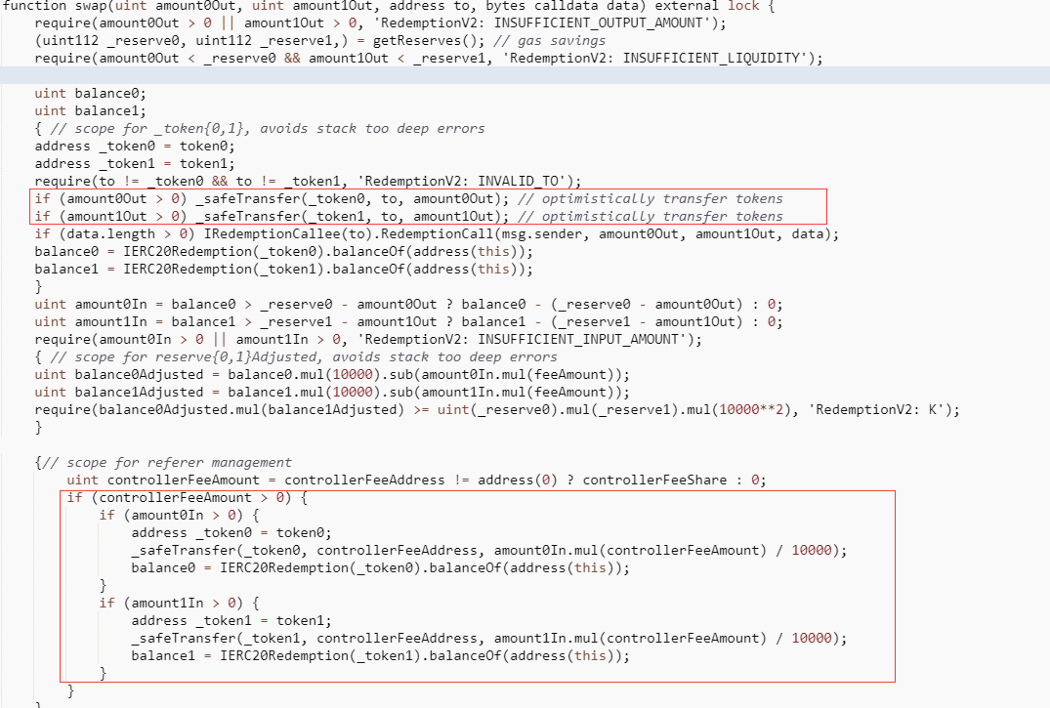
3. Since in the RedemptionPair contract, the controllerFee will be paid to the controllerFee address only after the swap, the attack contract did not lose any tokens by using 2omb to swap for 2omb (the swap fee is 0). Instead, the price of 2omb in RedemptionPair is getting higher.
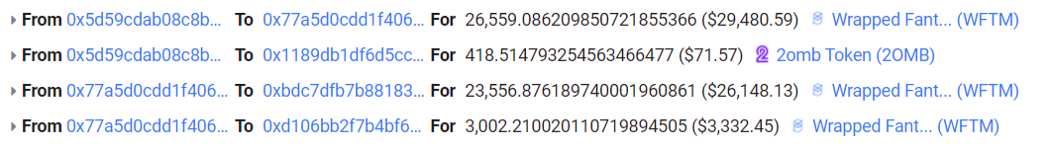
4. Swap all the profited 2omb for 26,559.086209850721855366 wftm, of which 23,556 to repay the flashloan, and the net profit is 3,002.210020110719894505 wftm.
5. Repeat the above steps.
Vulnerability Analysis
This attack mainly exploits the vulnerability that the swap fee rate in the RedemptionPair contract is 0 and the controllerFee fee collection occurs after the swap is completed.
The amountOut of the user exchange is not affected by the controllerFee fee while the reserve in the contract is reduced, thus affecting the price.
Fund Tracing
As of this writing, the stolen funds are estimated to be 74246.54966 WFTM, or about $81,671.
Summary
In response to this incident, Beosin security team recommends:
1. The handling fee is usually paid by the user and occurs before the user’s swap. When modifying the handling fee rate, attention should be paid to whether the modified value is reasonable and whether the process is safe.
2. Before the project goes live, it is highly recommended to choose a professional security audit company to conduct a comprehensive security audit to avoid security risks.
If you have need any blockchain security services, please contact us:
Related Project
Related Project Secure Score
Guess you like

Beosin Has Completed Security Audit Service of Crafting
April 21, 2022

2omb 3omb is currently being targeted by an arbitrage flash loan attack.
April 18, 2022

Beosin’s Analysis of the Beanstalk Exploit
April 18, 2022

Beosin VaaS — Smart Contract Automatic Detection Tool Officially Launched!
April 14, 2022
