October 09, 2022
BNB Chain’s $850 Million Hack — Using Beosin Trace to Investigate the Stolen Funds

On Oct 7, Beosin EagleEye monitored that BNB Chain’s cross-chain bridge BSC Token Hub was exploited for about $850 million, including $710 million on BSC and $143 million of bridged assets.
Attack Flow
BSC Token Hub uses a special pre-compiled contract for validating IAVL trees when performing cross-chain transaction verification. There is a bug in its implementation which may allow an attacker to forge arbitrary messages.
1. The attacker first picks the hash of a successfully submitted block (specified block: 110217401).
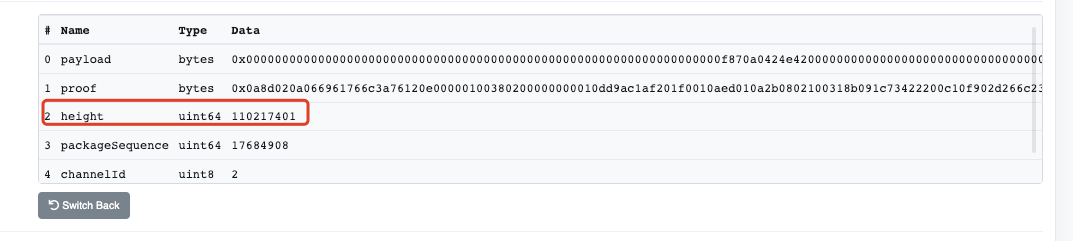
2. Then construct an attack payload as a leaf node to verify IAVL tree.
3. Add an arbitrary new leaf node to the IAVL tree.
4. At the same time, add a blank internal node to satisfy the implementation proof.
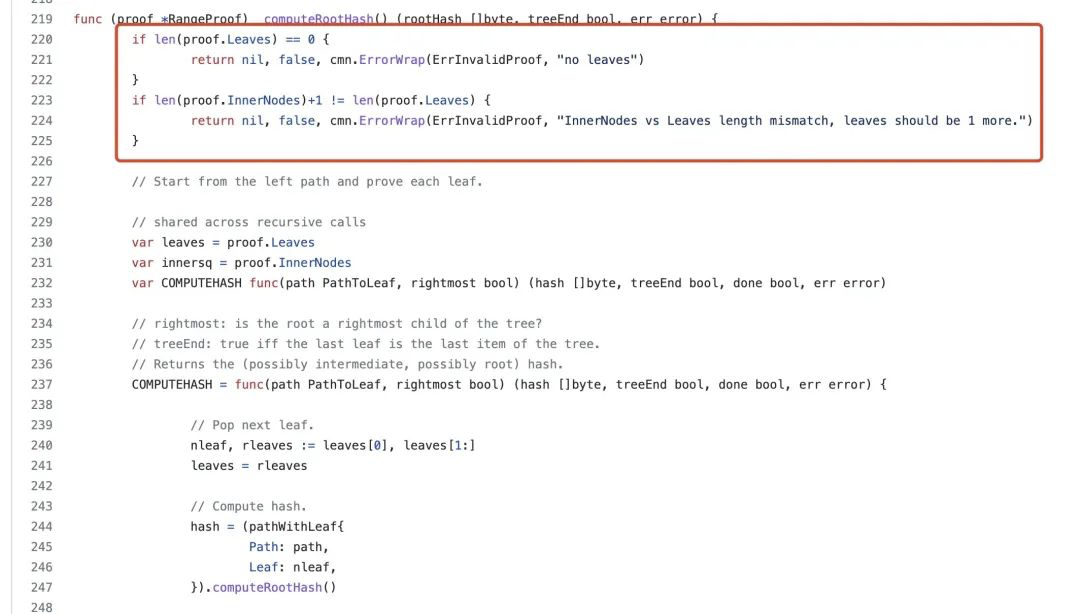
5. Adjust the leaf node added in step 3 so that the computed root hash is equal to the correct root hash selected in step 1 for a successful commit.
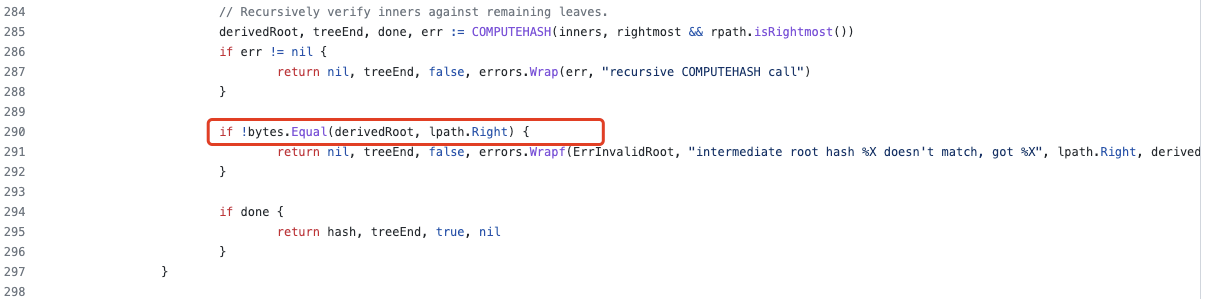
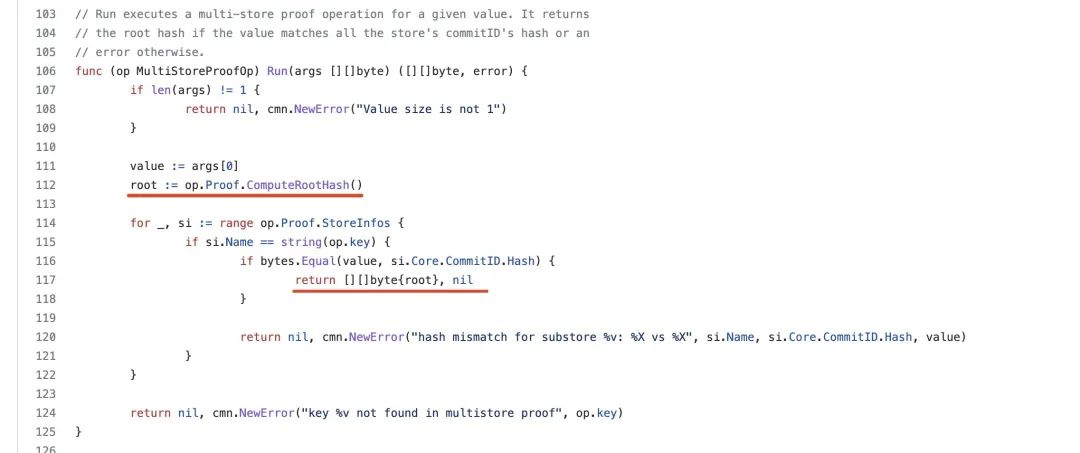
6. Finally construct the withdrawal proof for that particular block (110217401).
Vulnerability
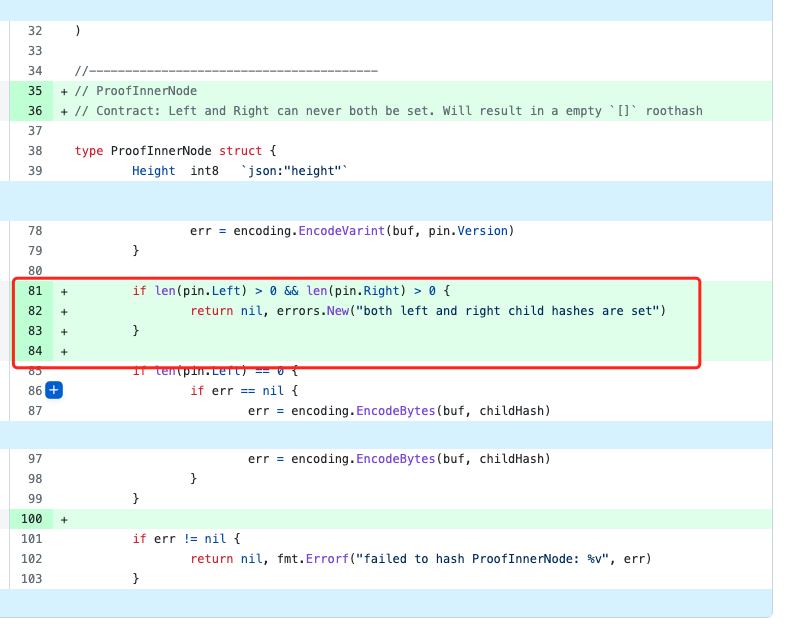
In the branch where len(pin.Left) is not 0, the hash calculation does not use the pin.Right data. The hacker uses this vulnerability to construct data and add proof.LeftPath[1].Right data, but this data is not involved in the hash calculation.
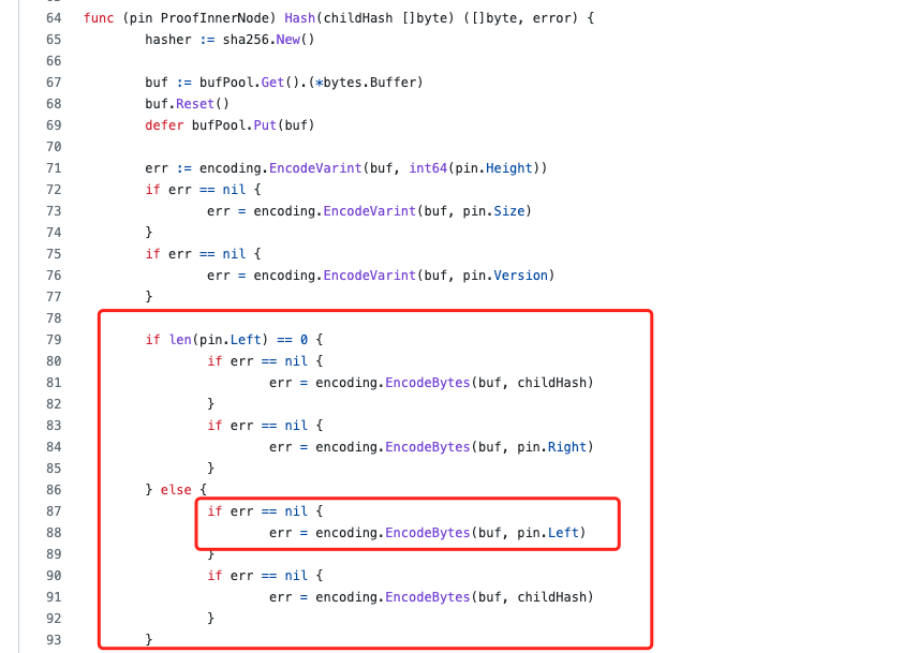
The current version has fixed.
Fund Trace
Using Beosin Trace — a crypto investigation and compliance tool, Beosin security team found that BSC Token Hub exploiter had bridged about $143.57M of the stolen funds to other chains (including lending). About $77.39M were bridged to Ethereum, ~$58.96M to Fantom (including gUSDT), ~$17.2M to Avalanche, ~$4M to Arbitrum, ~$400K to Polygon and ~$1.1M to Optimism.
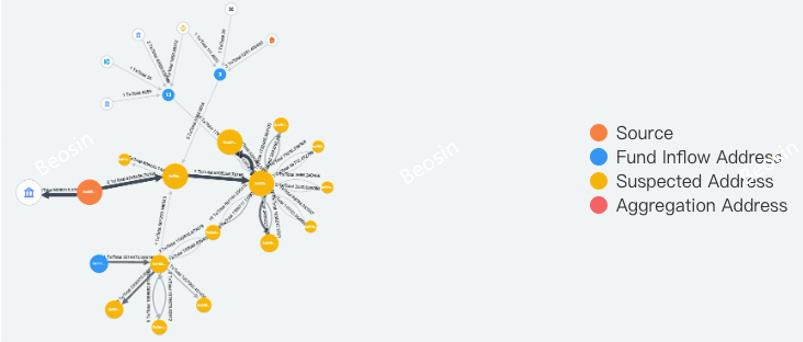
Trace Map from Beosin Trace
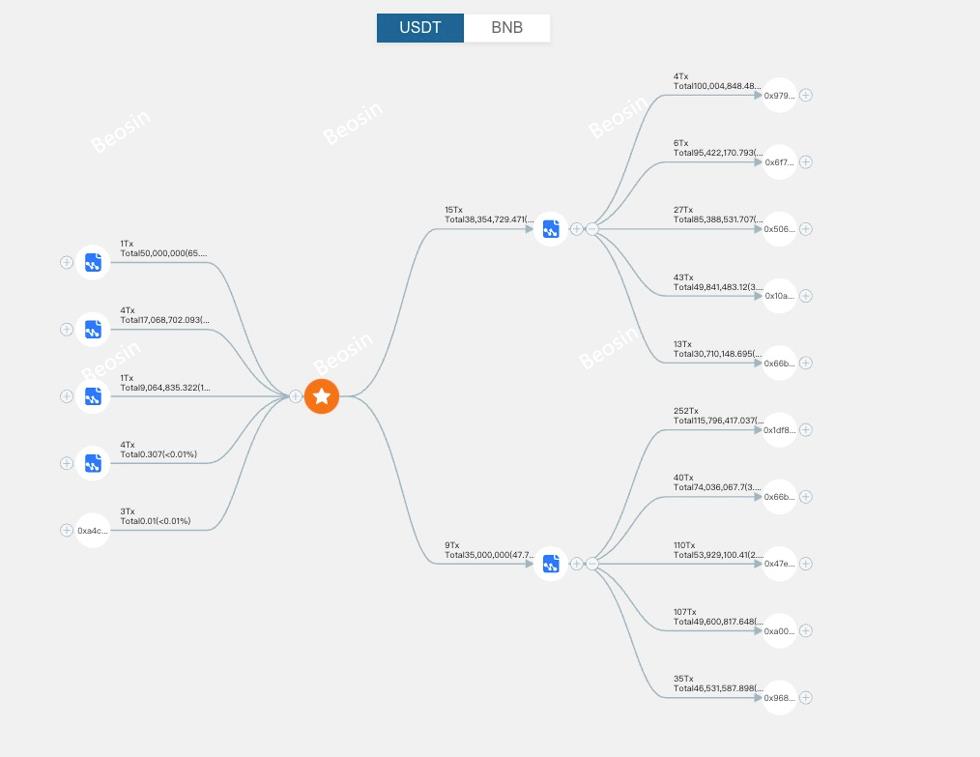
Trace Map from Beosin Trace
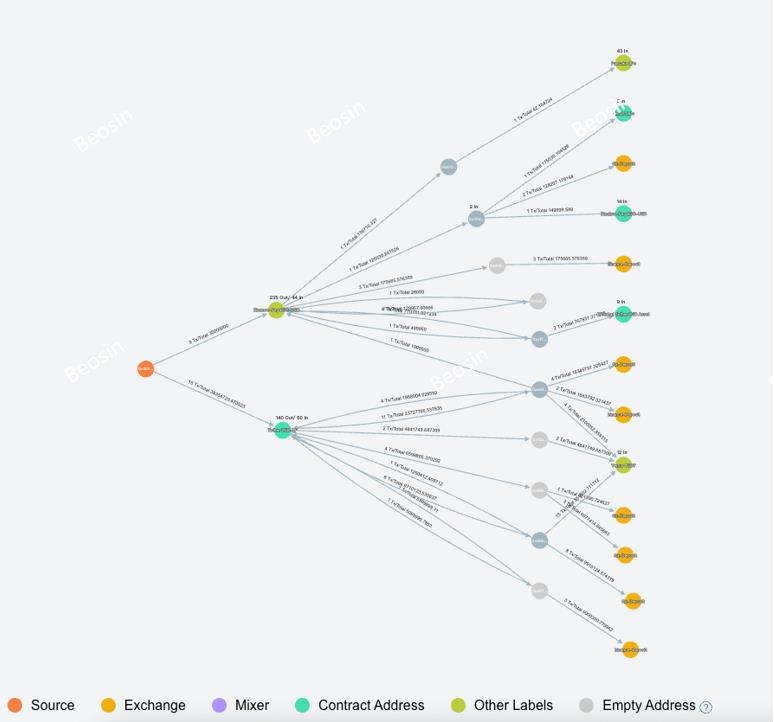
Trace Map from Beosin Trace
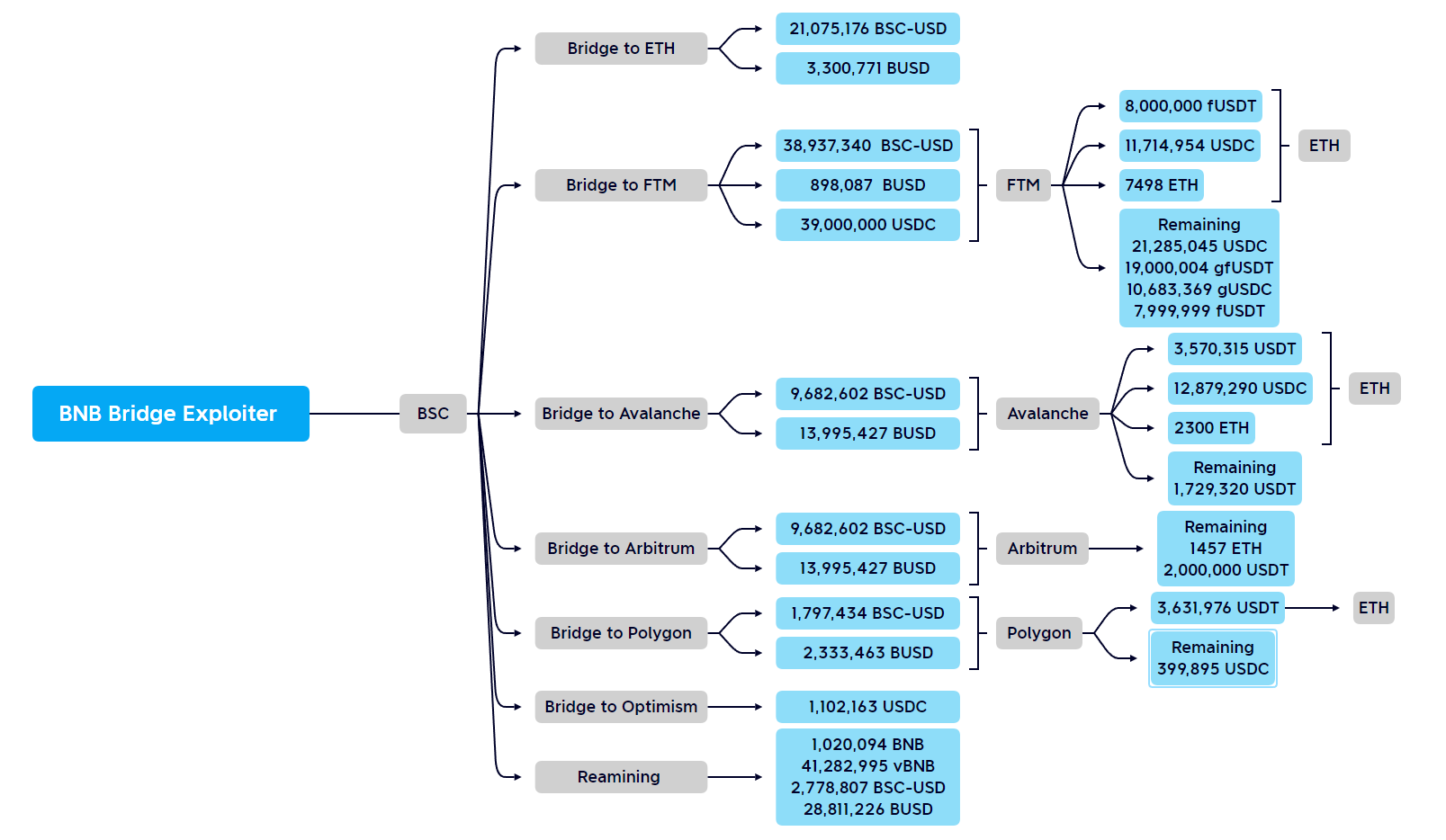
Funding statistics from Beosin Security Team
BNB Chain Back Online
BNB Smart Chain (BSC) resumed operations at around 06:40 Coordinated Universal Time (UTC). Beosin security team find that the current BSC node blocks the flow of stolen funds and potential attacks by blacklisting and suspending the iavlMerkleProofValidate feature.
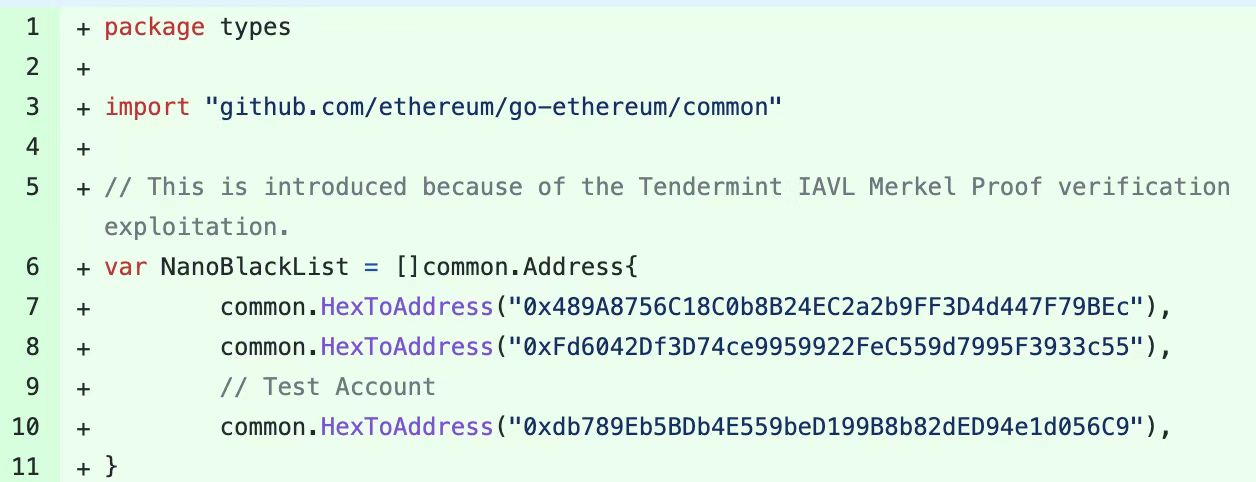
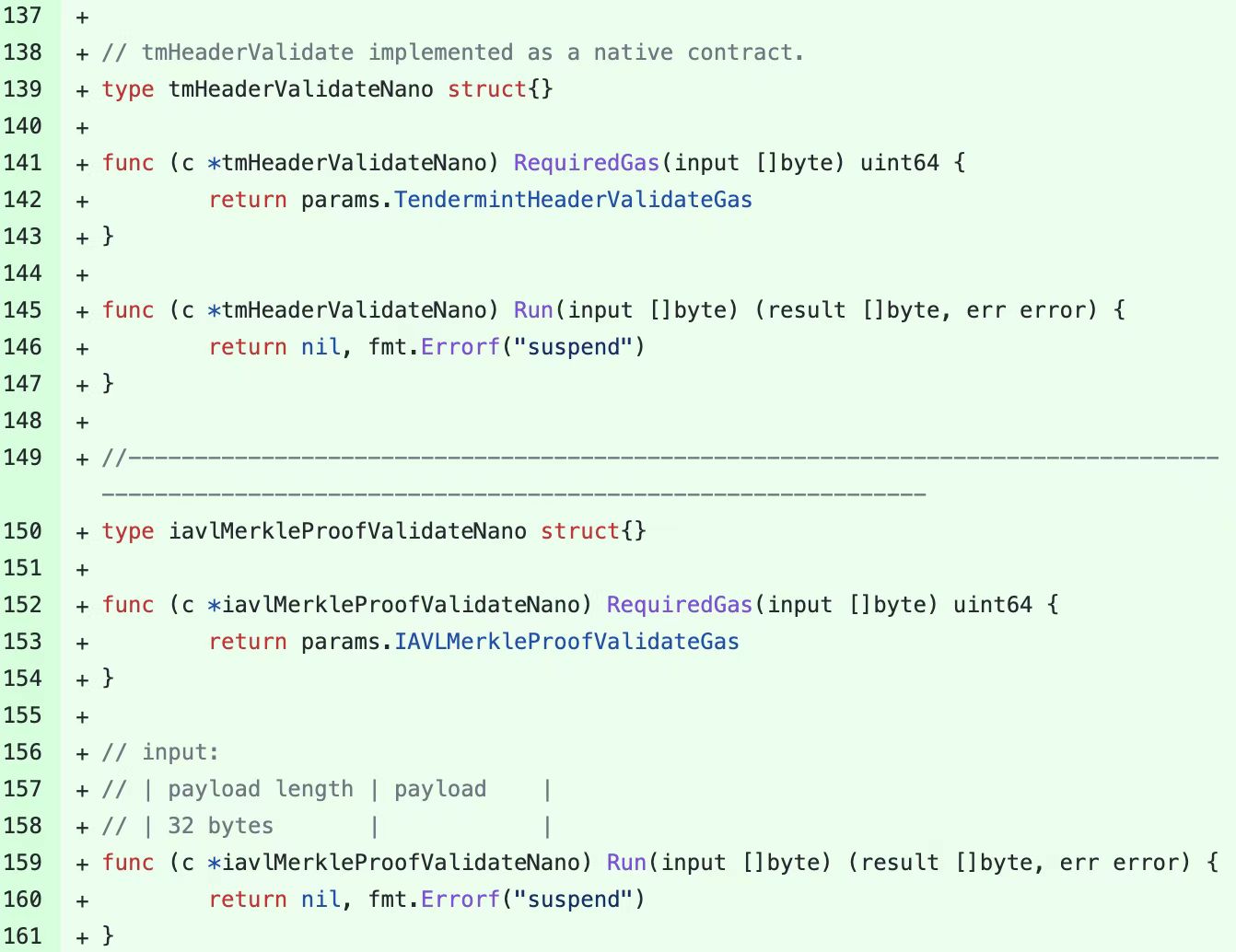
Cross-chain Bridge Security
Cross-chain bridges are usually projects with large amount of assets. The more code volume is, the more likely that some combinations of multiple vulnerabilities may occur. A high-risk point of cross-chain bridge is the off-chain security, because the on-chain and off-chain codes are generally audited separately, and off-chain security is usually guaranteed by the project itself, resulting in many vulnerabilities to be ignored.
Previous cross-chain bridge attacks are mainly from off-chain vulnerabilities or private key compromise. This time the exploit is through the construction of a specific root hash to construct a specific block of withdrawal proof. The attack is more sophisticated, and the amount is also higher than in the past. This incident also reminds us that vulnerabilities are often found in places we don’t expect, so the only thing is to keep improving the security of the project and discover these bugs earlier than those malicious actors.
For more cross-chain bridge related articles, please check our website at https://beosin.com/resources/
Contact
If you have need any blockchain security services, please contact us:
Related Project
Related Project Secure Score
Guess you like
.jpg)
Web3 Security Recap: $164.32 million lost in attacks in September
September 30, 2022

How Did the BNB Chain Exploiter Pass IAVL Proof Verification? — An In-depth Analysis by Beosin
October 09, 2022

Blockchain Security Alliance Held Its First Meeting to Secure the Web3 Ecosystem
October 11, 2022

Web3 Security Weekly Recap of M10W2
October 14, 2022
