September 27, 2023
ERC-7520 Proposal: zk-SNARK Public Inputs Overflow Protection

1. What is Zero-Knowledge Proof
Zero-knowledge proof (ZKP) is a cryptographic concept that allows one party (the prover) to prove to another party (the verifier) that a statement is true without revealing any additional information beyond the fact that the statement is true.
In a zero-knowledge proof, the prover can convince the verifier that a claim is true, and the verifier will only get one bit of knowledge — whether to accept or reject the claim — without learning anything else about the proof.
This concept can be explained with a simple example. Suppose there are two people, a prover and a verifier. The prover wants to prove to the verifier that he knows a secret password without revealing the password itself. In the traditional way, the prover would just tell the verifier the password. But with a zero-knowledge proof, the prover can use a special protocol to prove to the verifier that he knows the correct password without exposing the password itself.
Some common zero-knowledge proof systems and algorithms include zk-SNARKs, zk-STARKs, BulletProofs, etc.
2. Applications of ZKP in Blockchain
In blockchain technology, ZKP has various applications such as enhancing privacy, improving scalability and security. Here are some key applications of ZKP in blockchain:
- Privacy Protection: Blockchains are public which means anyone can view all the transactions on the chain. However, users may sometimes want to keep their transaction details private. ZKP allows users to prove they have enough funds to make a transaction without revealing their total account balance publicly. This greatly enhances users’ privacy protection. For example, Zcash uses zero-knowledge proof technology and is a cryptocurrency that allows users to conceal the sender, recipient, and amount of transactions.
- Computation Compression and Blockchain Scaling: Scalability is a challenge for blockchains, especially for large-scale applications. ZKP can help lighten the burden on nodes and improve overall system scalability. By using ZKP to verify the validity of transactions, nodes do not need to look through the full transaction history, reducing storage and computation load. ZK Rollup is a scaling solution that combines Rollup and ZKP to improve throughput and efficiency of Ethereum and other blockchains. Instead of validating and recording every transaction on-chain like in traditional Ethereum, ZK Rollup batches many transactions off-chain and uses ZKP to prove the validity of the batch, ensuring correctness and security while significantly improving scalability.
- Identity Verification: Zero-knowledge proofs can be used to validate a user’s identity without revealing sensitive personal information. For example, someone could use a ZKP to prove to the network they meet a certain age requirement or hold a specific certificate without revealing their exact age or other identifying details.
- Decentralized Storage: Servers can prove to users that their data is being properly stored without revealing any contents of the data.
In summary, blockchain ZKP has broad applications in privacy protection, computation compression and scaling, identity verification, decentralized storage, and more. It provides blockchains with more functionality and choices, advancing blockchain development and adoption across different domains.
3. Double-Spending Attack in ZKP Applications
Zk-SNARK (Zero-Knowledge Succinct Non-Interactive Argument of Knowledge) is a zero-knowledge proof technology that can prove the validity of a statement without revealing real information. It is a very efficient zero-knowledge proof that can generate and verify proofs very quickly while protecting privacy and security, and therefore has been widely adopted. However, with the expansion of its applications, security concerns have also increased.
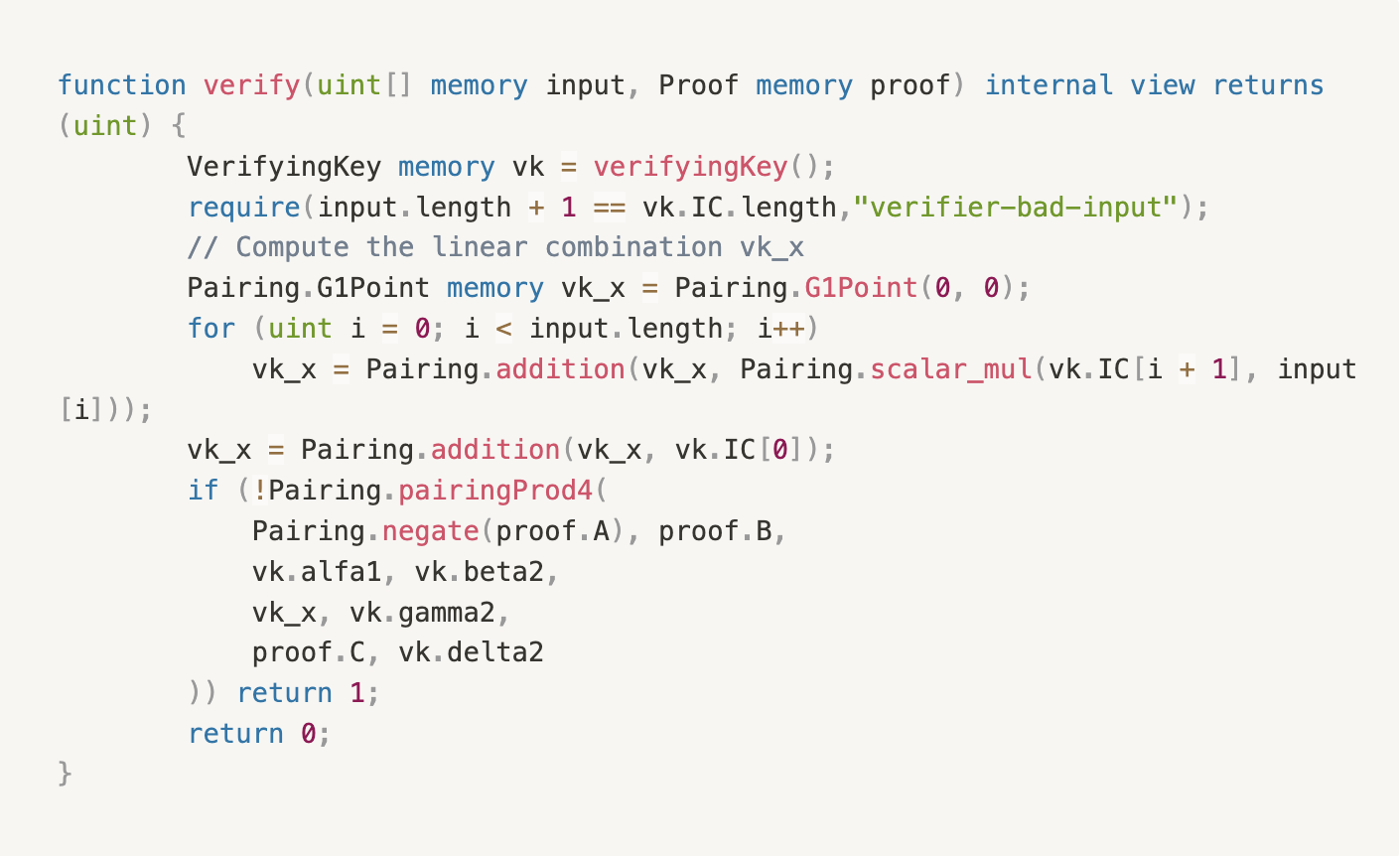
A common vulnerability was previously discovered by Beosin: if the input value range is not properly checked in the verify function of ZKP projects, attackers can forge multiple fake inputs to pass verification and cause double spending. This attack affects many zk-SNARK algorithms including groth16, plonk, and multiple languages like Solidity and JavaScript.
This vulnerability was first discovered by poma in the Semaphore ZKP project, who provided two example transactions of successful attacks, as shown below:
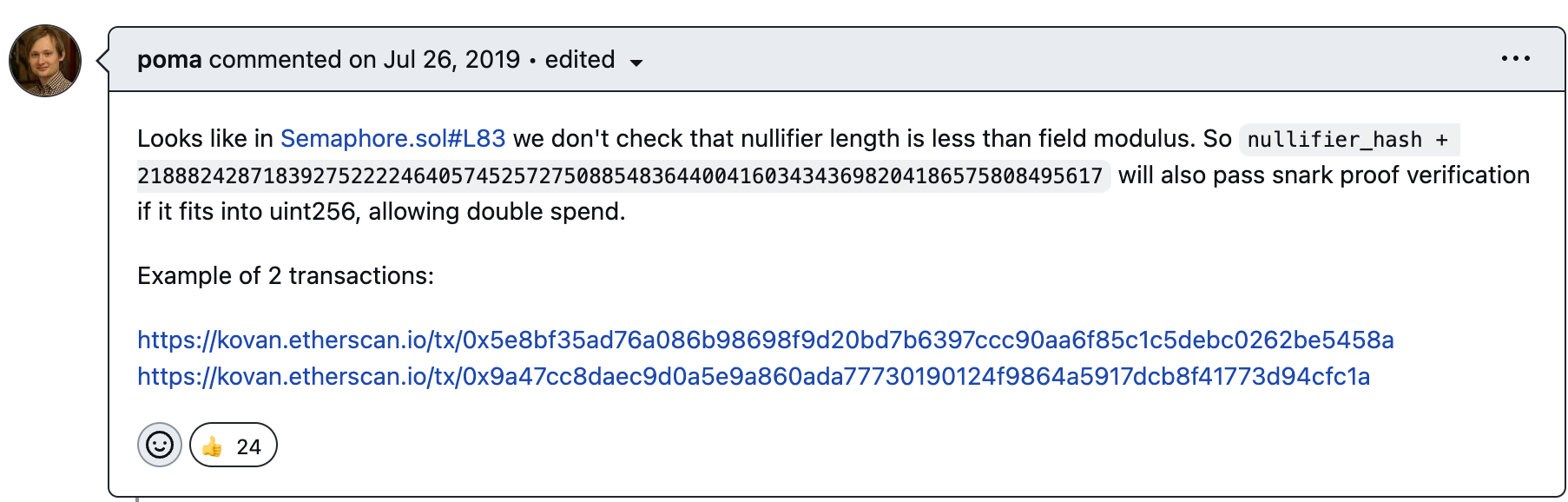
https://github.com/semaphore-protocol/semaphore/issues/16
The attack principle is that to generate and verify zk-SNARK proofs on Ethereum, F_p-arithmetic finite field elliptic curve circuits need to be used, where the p value determines the range of the finite field of the elliptic curve, so the input value range of the circuit is [0, 1, ..., p-1]. Different curves have different p values:
BN254 curve defined in EIP-196 (also known as ALT_BN128 curve):
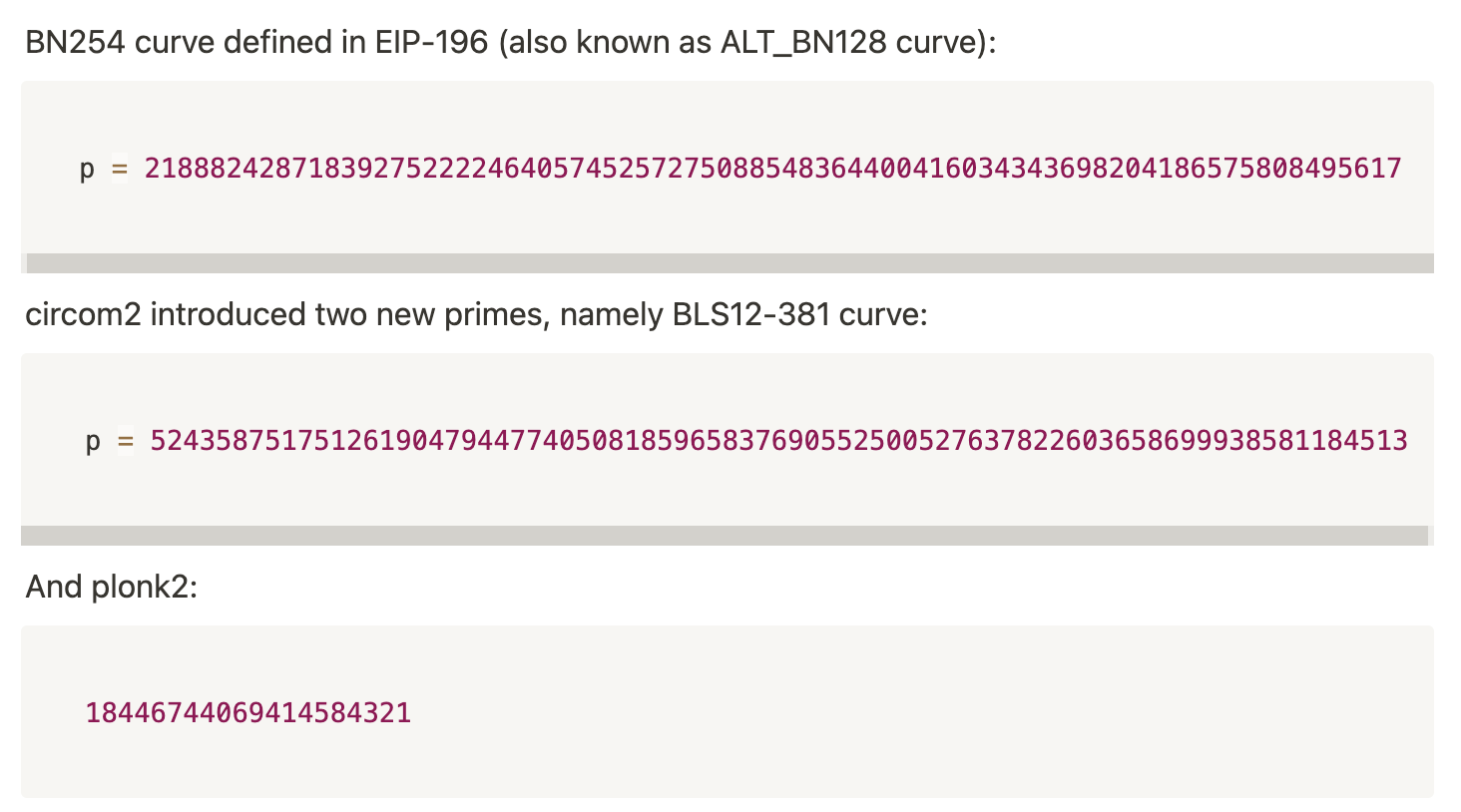
However, when implementing the verification code, the integer variable types in different programming languages can be much larger than the input value range of the circuit, such as: uint256 in solidity can represent [0,2^{256}-1], long int in java is [-2⁶³,2⁶³-1], bigint in javascript, etc. In this case, multiple inputs can pass the verification after modulo p operation in the verification code:
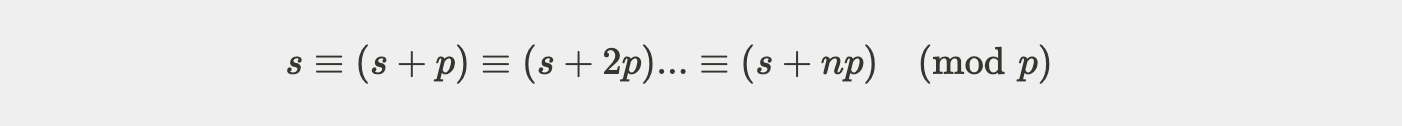
In summary, as long as any valid proof parameter x is known, values of s+np(n = 1,2,…,n)within the variable range can pass the verification. So if the attacker gets any verified x, he can construct max(uint256)/p of s’ that pass the verification. The specific attack flow is as follows:
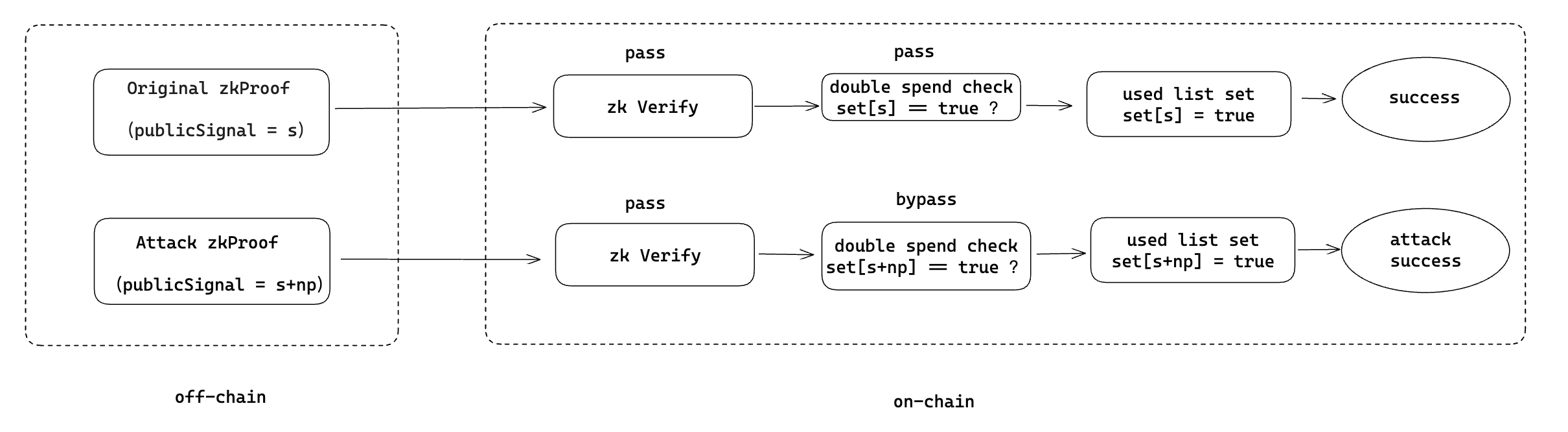
Semaphore later confirmed and fixed this bug, and zk libraries like ZoKrates and snarkjs also released emergency patches. However, Beosin researchers found there is not yet a unified solution. For example, the Semaphore protocol applies constraints at the pairing library level without explicitly checking data validity range in outer business logic, while the contract code generated by circom and Tornado.Cash explicitly check the SNARK_SCALAR_FIELD in the verify function. Such inconsistent fixes could confuse and endanger many new zk DApp projects. Therefore, we hope a standardized solution can be used to resolve this issue.
4. Double Spending Attack in ERC-1922
Ethereum currently has a zk-related standard EIP-1922 that introduces a standard interface for verifying zk-SNARK proofs, with code as follows:
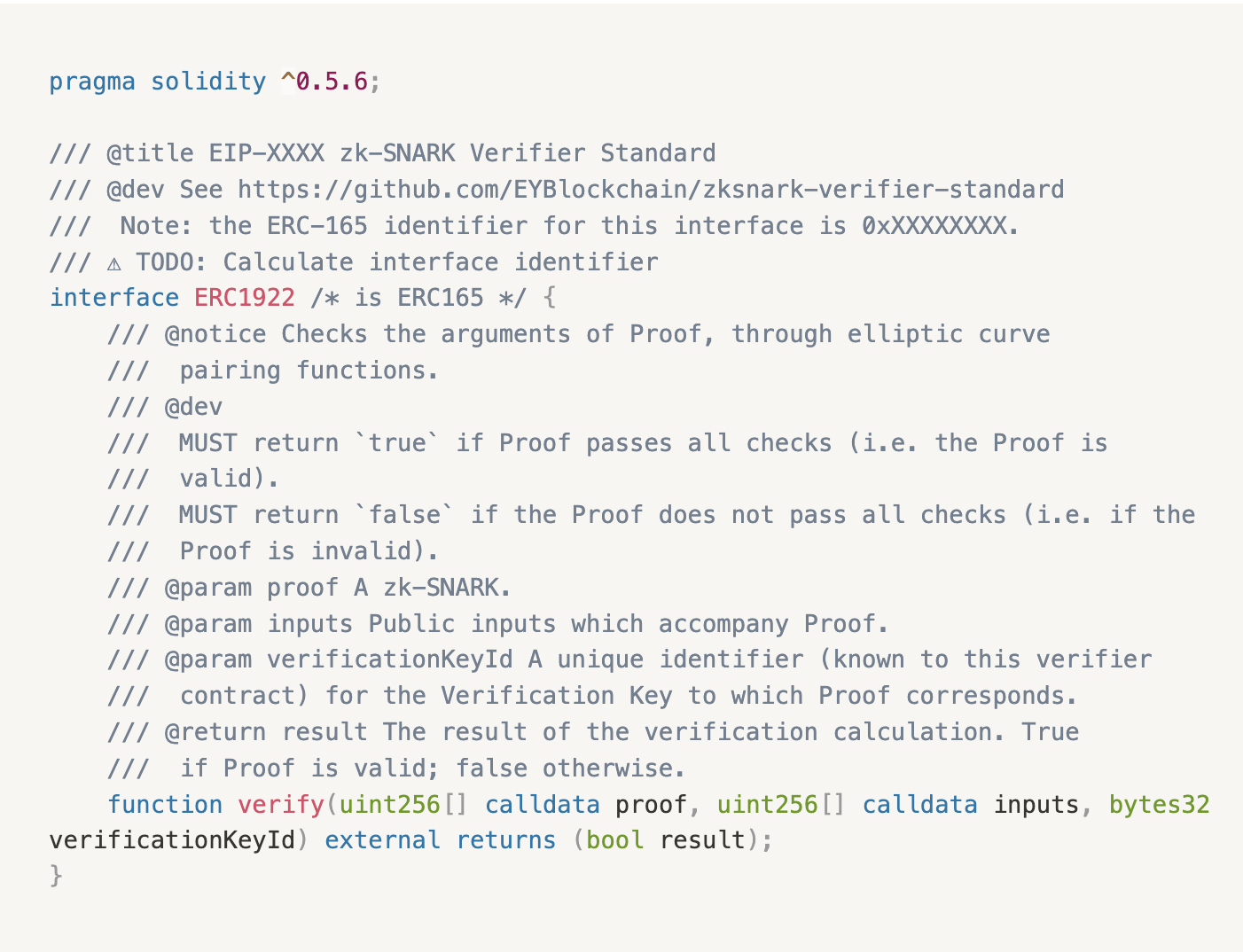
The proof and inputs variables are uint256[] types commonly used for elliptic curve operations in ZKP algorithms. But this interface does not include corresponding security protections, and thus also suffers from huge security risk of double-spending attacks.
5. ERC-7520 Solution
Based on the above problems, Beosin proposed EIP-7520 to mitigate these security risks. Specifically, all DApp projects using zk technology in the Ethereum ecosystem must implement this interface in their compliant verifier contracts to validate input ranges in a standardized, unified, and secure way:
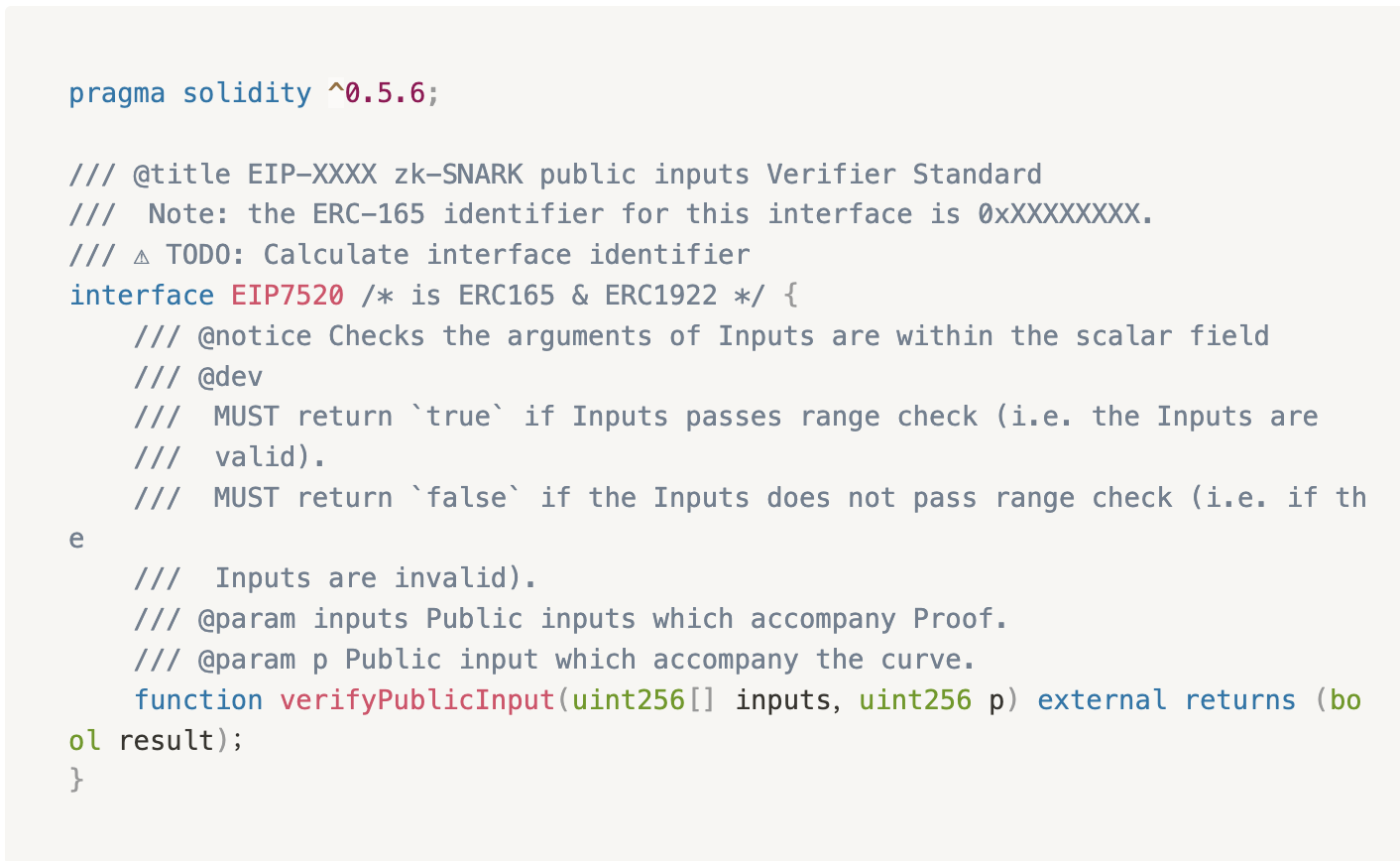
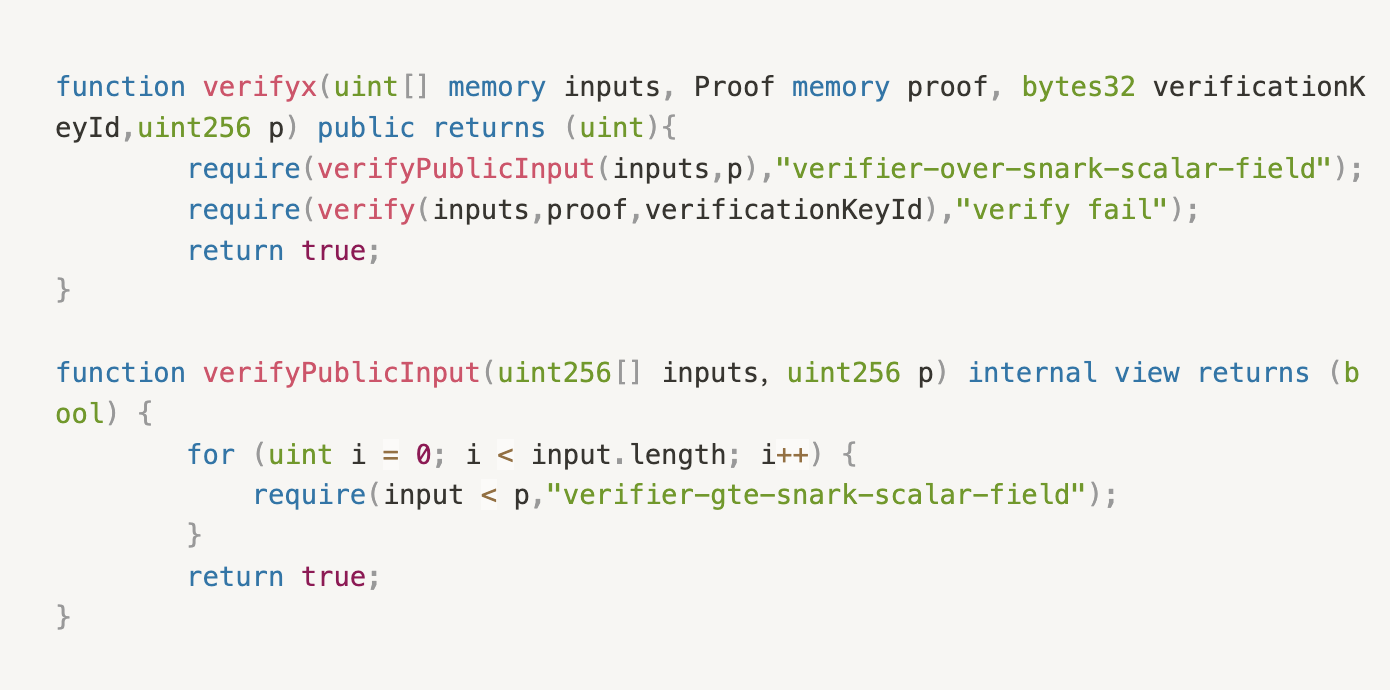
The verifyPublicInput function is the core of this standard. The parameters are:
inputs: Defined asuint256[]type, representing the public signal parameters involved in the verify function of the ZKP project.p: Defined asuint256type, corresponding to the prime p value of the elliptic curve used in the algorithm.
Next we will demonstrate the different behaviors against this attack with and without implementing the EIP-7520 interface, to show the risks to projects:
- If we directly use the verify contract code for proof verification without calling the verifyPublicInput interface, as below:
Screenshot of the original results that the proof verifiaction passed:
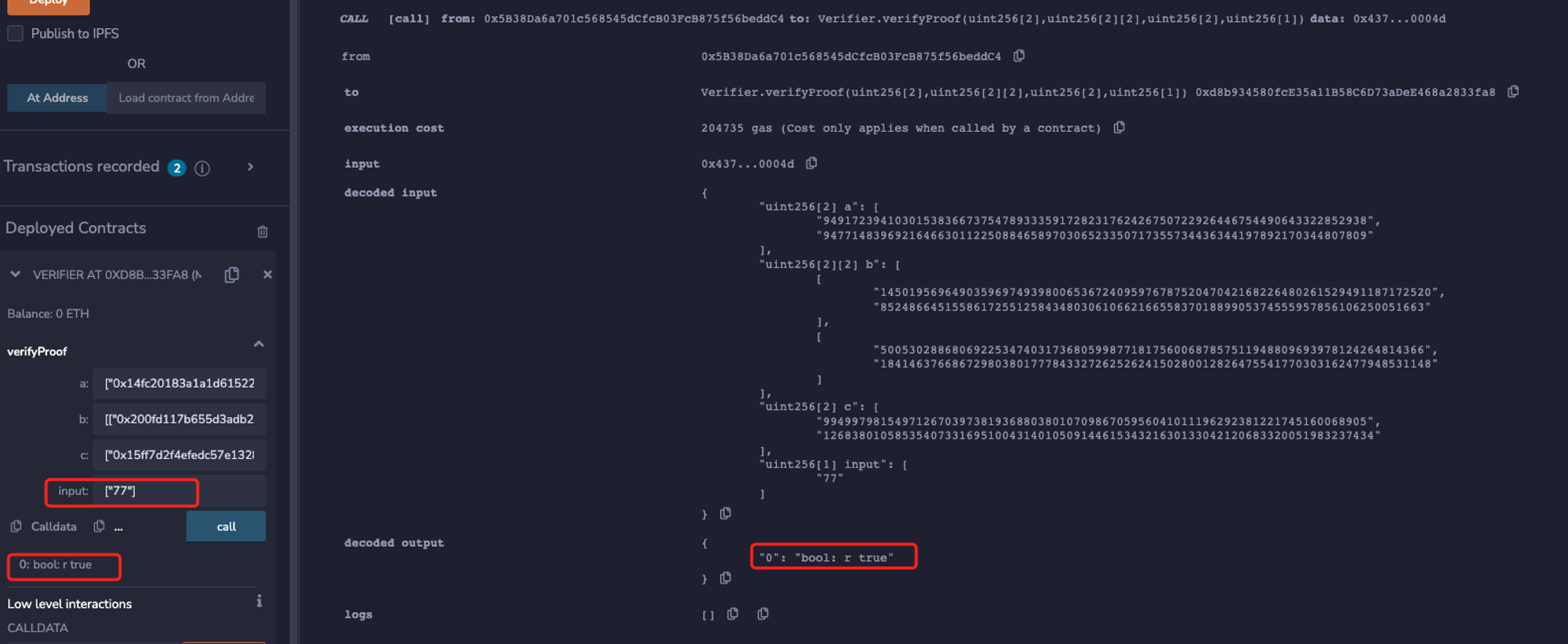
At the same time, the following 4 forged proofs can also pass the verification, causing double spending attack:
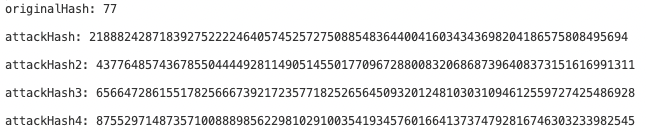
Use one of the forged proofs, the verification result is as follows:
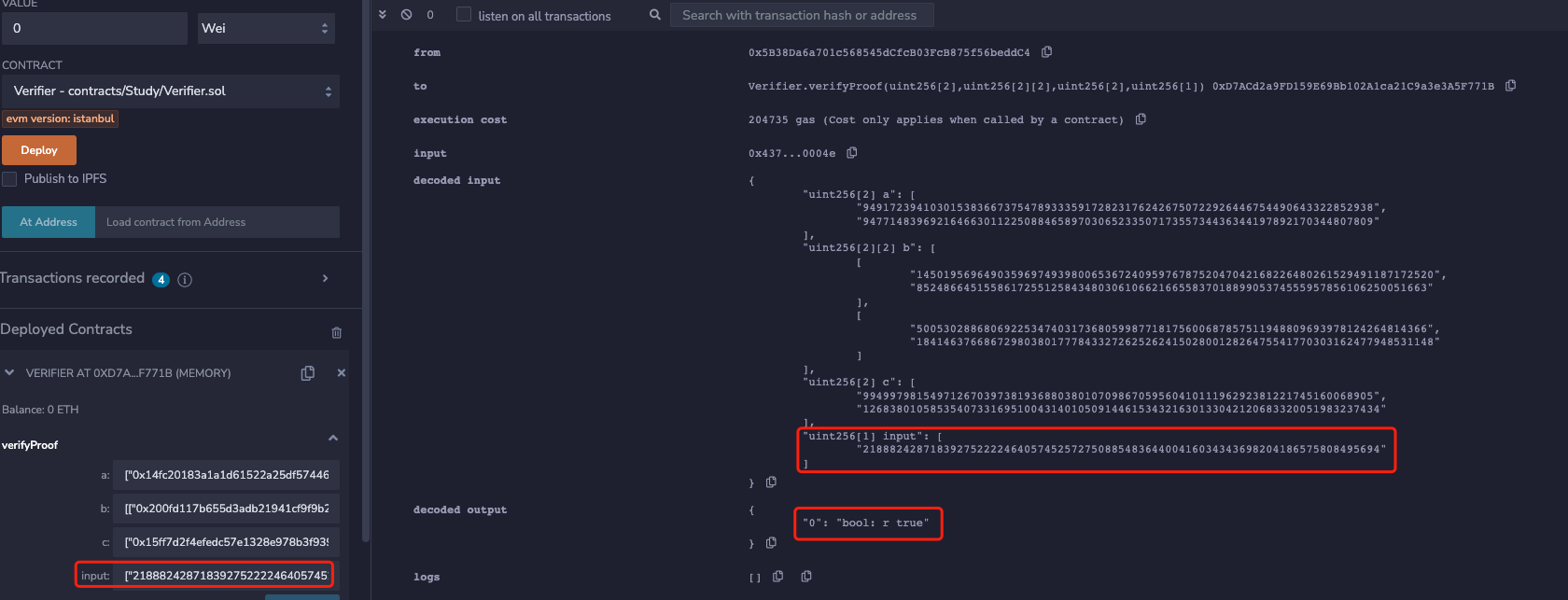
2. If the verifyPublicInput interface in this eip is called, the verification of the above forged proof will fail. Part of the contract code is as follows.
The experiment result is as shown below:
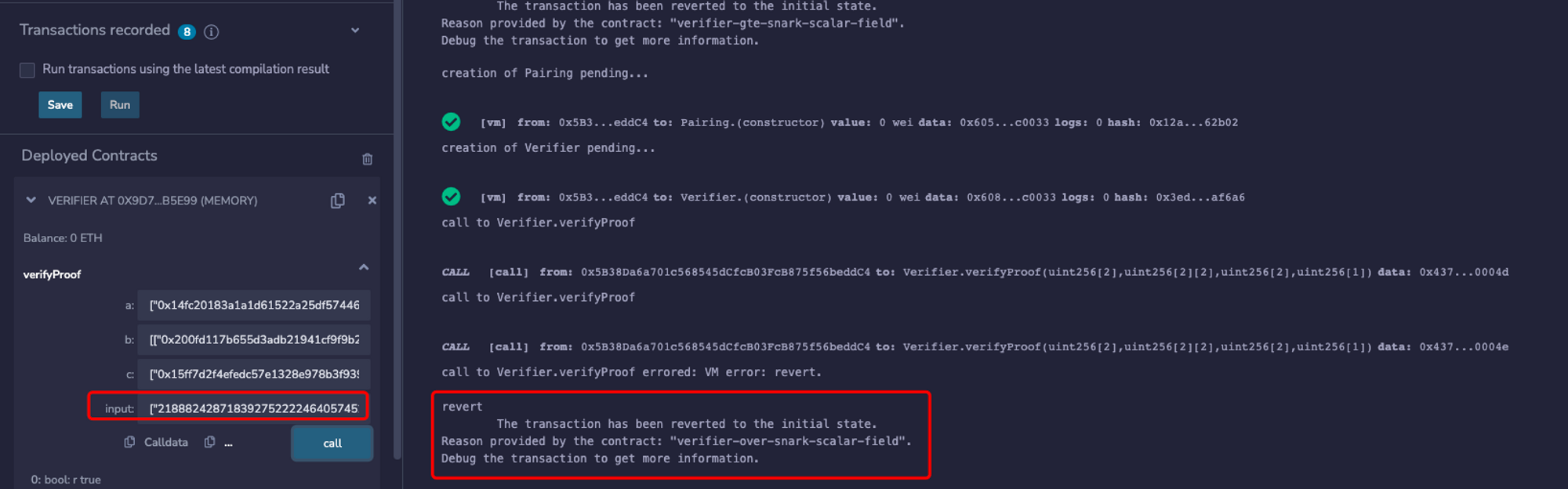
In summary, if the validity of public input value range is not checked using this interface, the risk of double spending attacks may exist.
Contact
If you need any blockchain security services, welcome to contact us:
Related Project
Related Project Secure Score
Guess you like

Q3 2023 Global Web3 Security Report, AML Analysis & Crypto Regulatory Landscape
September 27, 2023

Q3 2023 Global Web3 Security Report, AML Analysis & Crypto Regulatory Landscape
September 27, 2023

The 3rd Wave of Technological Advancements in Blockchain: Exploring Application of ZKP Technology
October 09, 2023

Beosin Forms Strategic Partnership with Cryptocurrency Payment Platform RedotPay
October 13, 2023
