June 24, 2022
Harmony Bridge Hacked for $100M due to Suspected Private Key Compromise
On June 24, Harmony Bridge was hacked for about $100M due to suspected private key compromise. Here’s our analysis of this incident.
Background
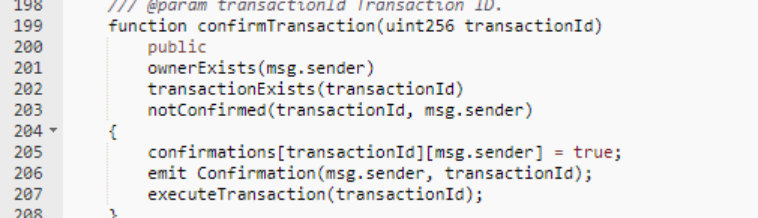
Harmony Bridge is a cross-chain bridge with five validators for operational verification. The main reason for this attack is that the private keys of two validators are suspected to be compromised, resulting in the confirmTransaction function of the contract to be called successfully.
Attack process
Hacker address:
0x0d043128146654C7683Fbf30ac98D7B2285DeD00
Addresses with suspected private key compromise:
0xf845A7ee8477AD1FB4446651E548901a2635A915
0x812d8622C6F3c45959439e7ede3C580dA06f8f25
Victim contract:
0x715cdda5e9ad30a0ced14940f9997ee611496de6
Example hash:
0x6e5251068aa99613366fd707f3ed99ce1cb7ffdea05b94568e6af4f460cecd65
Related transactionId:
21106–21118(ETH),120515–120518(BNB)
The private key compromise address 0x812d86 calls the confirmTransaction function of the 0x715cdd contract for operation verification, and the transactionId for verification is 21107 (here the transactionId of 21107 is used as an example).
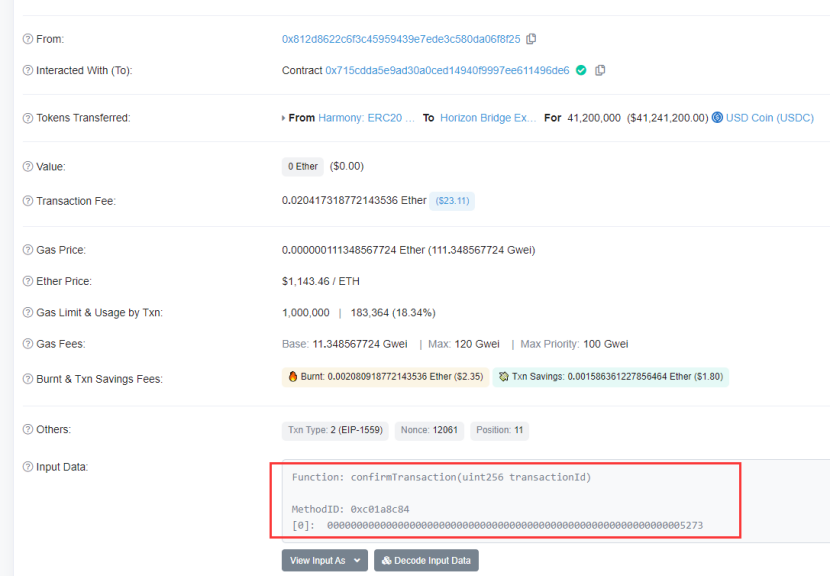
It can be found that in this transaction, the validation of isConfirmed returns true.
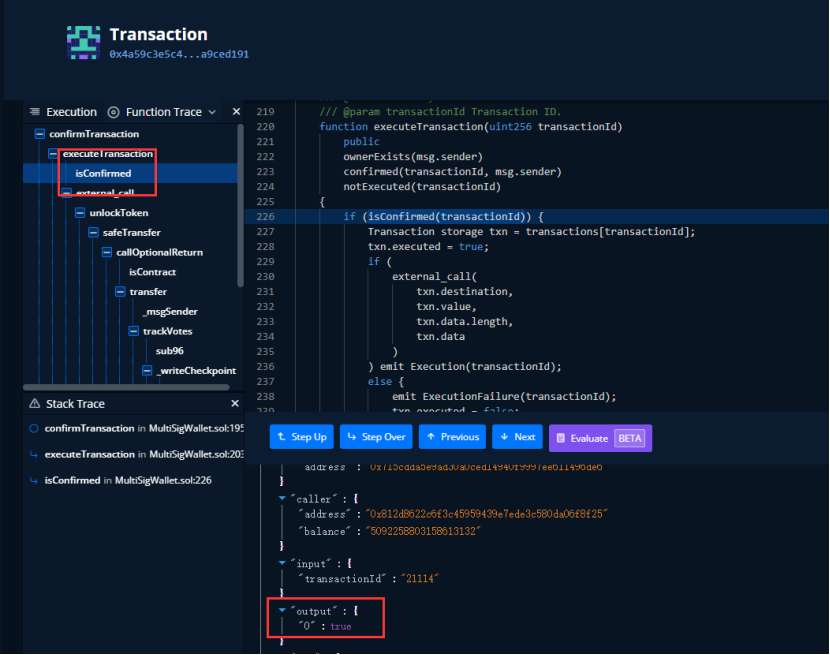
However, a validator node query in the contract shows that although there are five owners, only two have been verified.
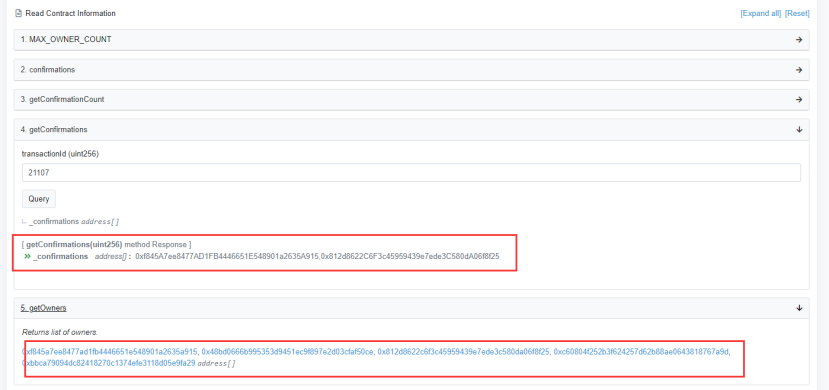
The attacker then uses these two validator nodes to successfully get the corresponding tokens using external_call and repeatedly exploits this attack to profit.
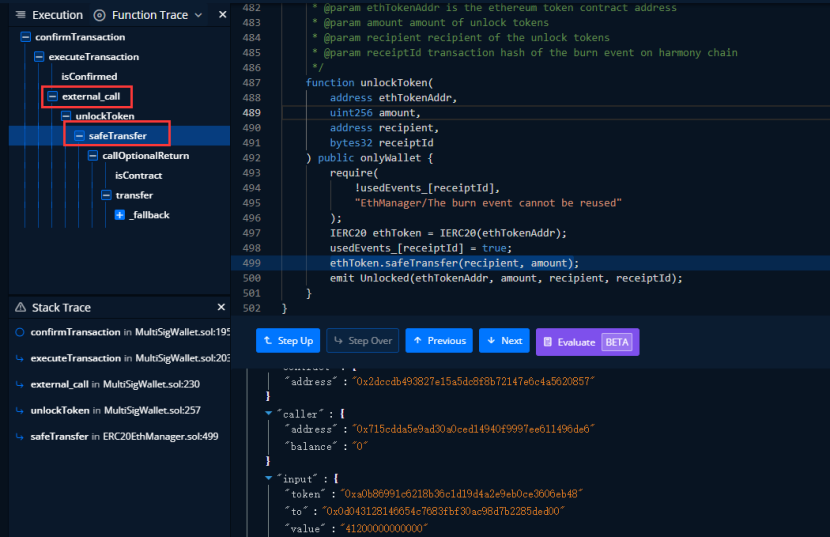
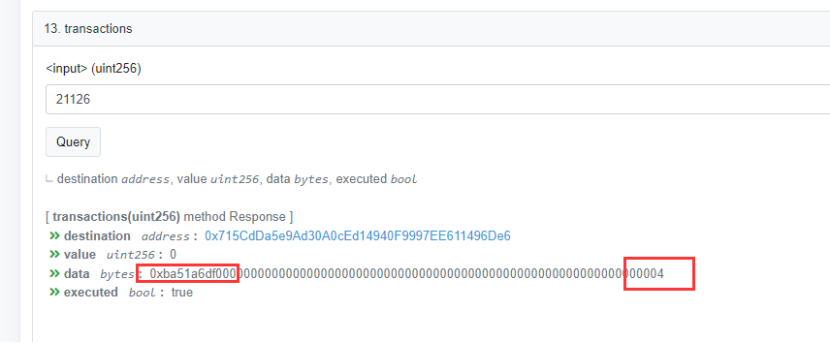
The project subsequently changed the number of validator nodes required to pass from 2 to 4 via transactionId of 21126 (120531 on BNB Chain).
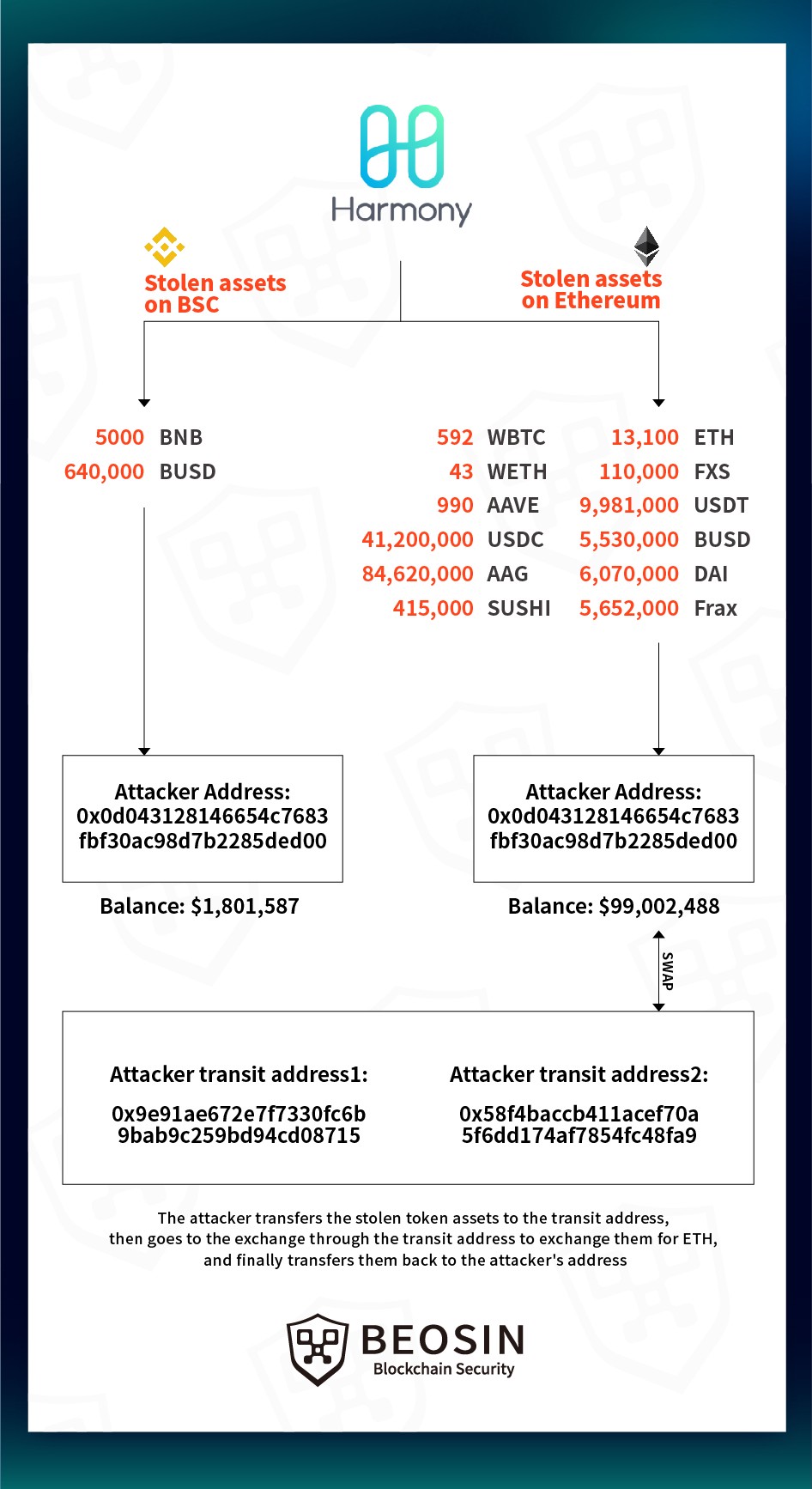
Fund Flow
The attack resulted in the loss of 85,867 ETH, 990 AAVE and 78,500,000 AAG on Ethereum, and 5,000 BNB and 640,000 BUSD on BNB Chain, for a total of about $100,428,116. The stolen funds are still held at the attacker’s address.
Summary
The attacker took advantage of the low number of validator node verification requirements and used two validator nodes to steal millions of dollars in assets. It is recommended that the project owner try to choose more nodes when designing the number of validator verification requirements and do a good job of validator security.
More
2. How to Ensure the Security of NFT Under the Web 3.0 Boom?
3. A Research Into NFT Whitelist Bypass Vulnerability (1/2)
4. Investigation of Common Phishing Attacks in Web 3.0: Discord, Google Ads, Fake Domains and Others
5. 「RECAP」AMA About How to Keep Your Smart Contract Secure During Development With Beosin VaaS
6. Hype, Plagiarism, Insider Fraud, NFT Scams on OpenSea and Security Advice
Contact
If you have need any blockchain security services, please contact us:
Related Project
Related Project Secure Score
Guess you like

A Research Into Vulnerabilities in NFT Platforms
June 28, 2022
.png)
A Research Into NFT Whitelist Bypass Vulnerability
June 24, 2022
.png)
Hype, Plagiarism, Insider Fraud, NFT Scams on OpenSea and Security Advice
July 25, 2022

Creating a $9 billion valuation in 5 years: what is Optimism?
June 07, 2022
